OWASP Juice Shop can be downloaded and run via the OWASP website itself but I preferred the tryhackme version as there is an option to deploy it and they sort of tell you what you’re looking for while making you answer questions to make sure you’re following along.
Task 1: Deploy the machine
This is standard procedure on tryhackme where you get the ip of your deployed machine after you use openvpn to connect to their network. Tryhackme has more instructions on how to do this.
Task 2: Set up burp
This is not necessary but it helps to have burp set up and using it. Tryhackme has more instructions on how to do this.
Task 3: Walk through the application
This is a common step to all web based ctfs and other labs. This is for you to understand and use the app/website in question. This helps you understand the business logic and then find potential areas to exploit. If you are already running burp suite with the proxy it will passively crawl the website as you keep visiting different parts of the website. This is essentially click every link, use every functionality and see the results.
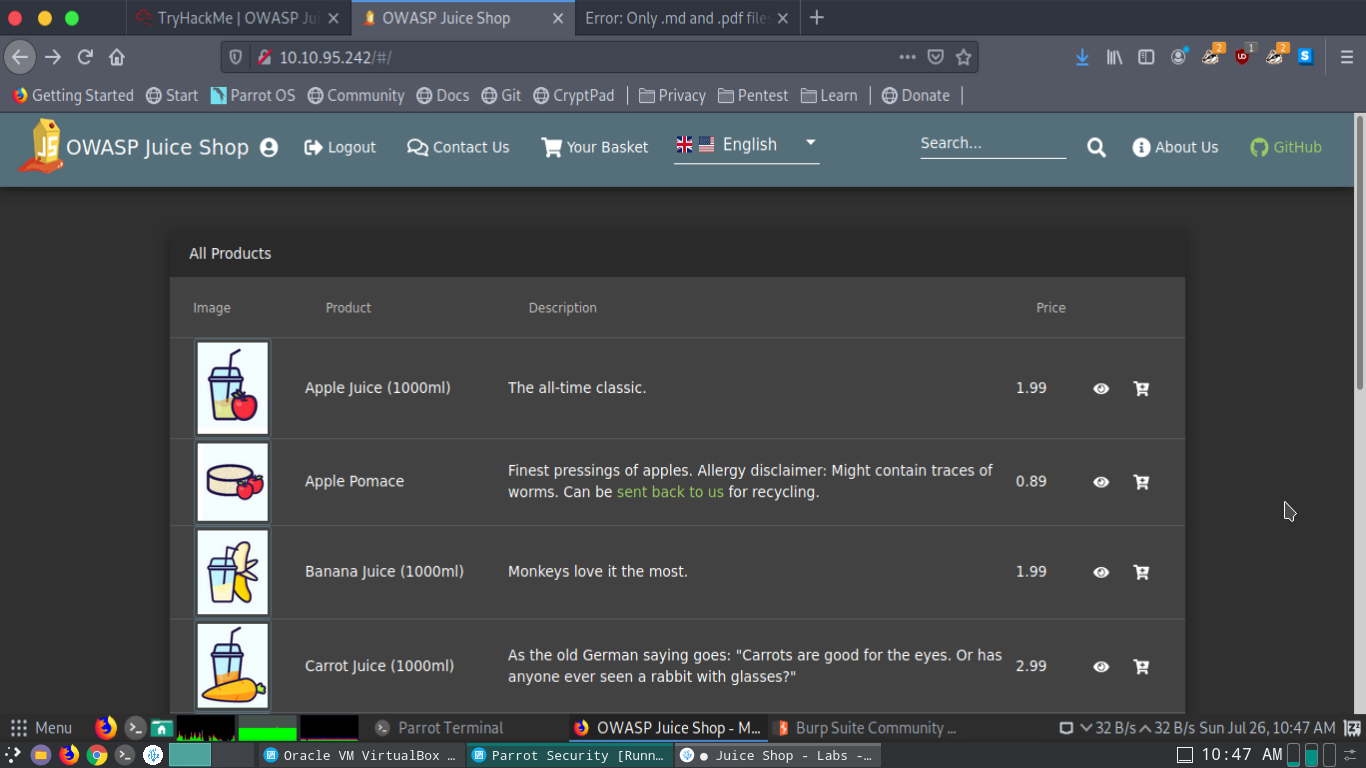
As I was going through the website I found a link (http://10.10.95.242/ftp/legal.md?md_debug=true) to their terms and conditions with an ftp directory. Simply keeping it as ftp/ it showed a bunch of files and one folder which revealed that there is Ubuntu running and Express running as well. Node is installed as well.

Task 4 : Injection
There are two types of injection in question,
- SQL Injection
- Command Injection
For this we are using only SQL Injection to log into the admin account.
While going through the website there was a review to the apple juice product by an admin@juice-sh.op account. So now we have the admin email.
admin@juice-sh.op' OR 1=1 --
was used as the username and the password was randomly inputted to login successfully.
Task 5 : Broken Authentication
- Forgotten password mechanisms
- Exploiting bugs in the authentication process
Reset Jim’s password using the forgotten password mechanism - what was the answer to the secret question?
Going to the Forgot Password Page it showed after you enter the email it requires the answer to a security question. What is the middle name of jims older brother.
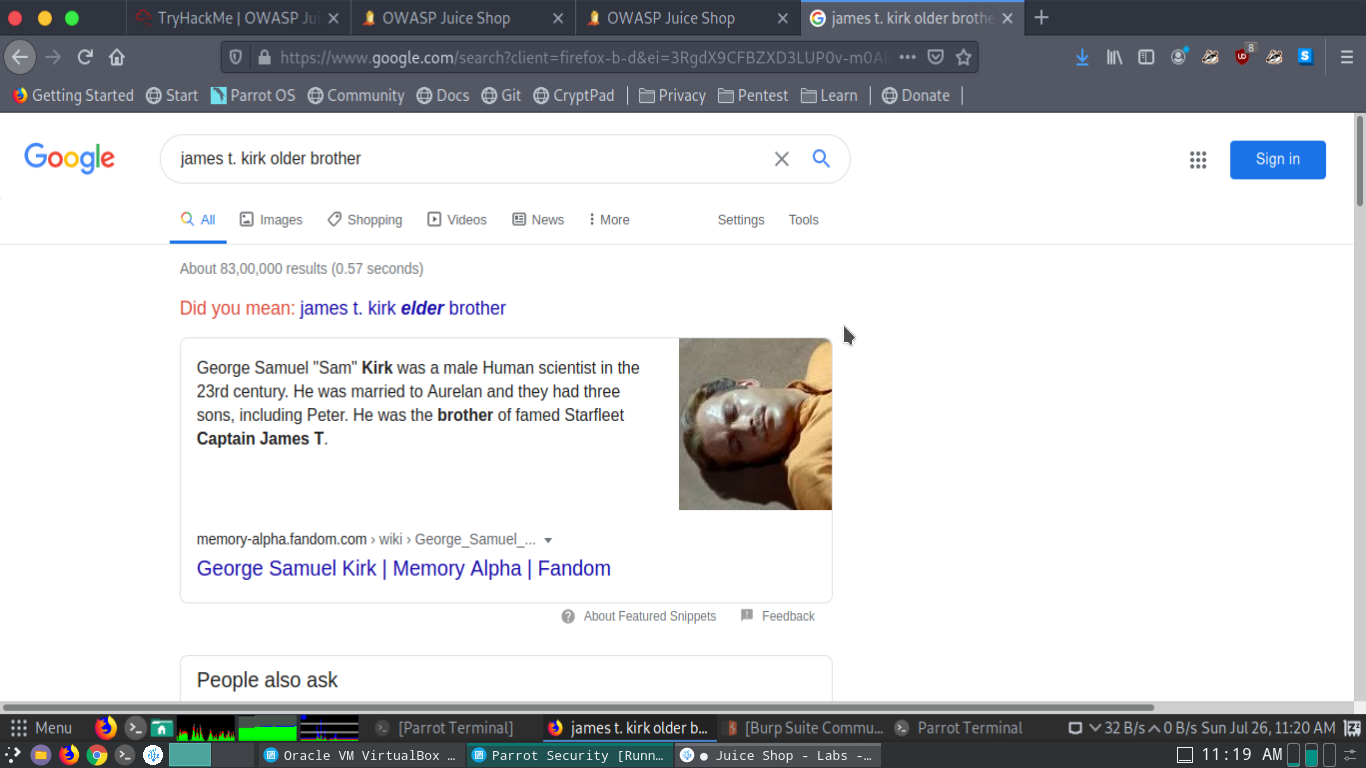
Firstly I need to find what the email/username is, searching through the reviews for products I found jim@juice-sh.op. This seems to be the email(juice-sh.op) for all accounts maybe useful as I keep doing it. As I was going through the reviews jim seemed to reply to another review mentioning a starfleet logo. A google search revealed it as James T. Kirk part of the Star Trek universe.
What is the administrator password?
Since it was an admin account I tried common admin passwords, ‘admin’, ‘administrator’ didn’t work but ‘admin123’ worked
Task 6 : Sensitive Data Exposure
Access a confidential document and enter the name of the first file with the extension “.md”
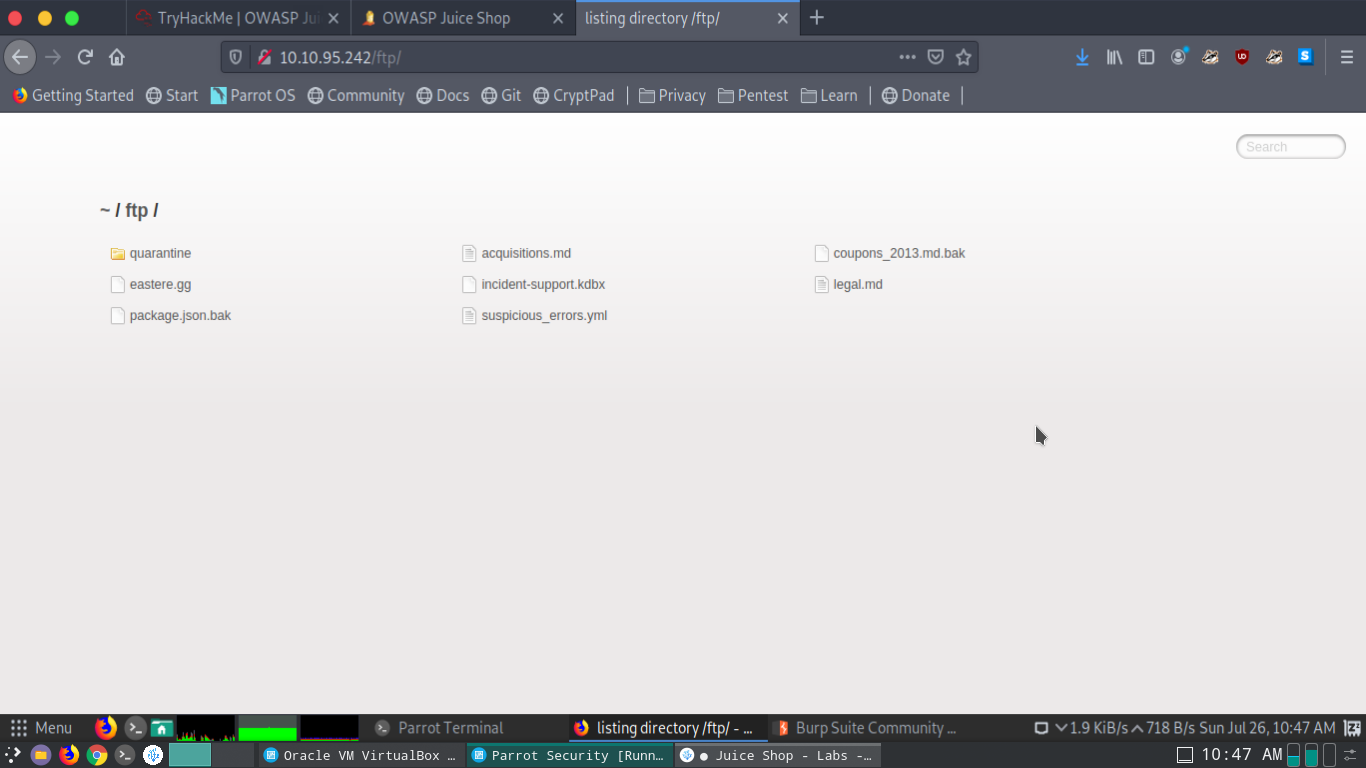
During the application walkthrough I discovered the ftp folder had the acquisitions.md file which contained the sensitive data.
Task 7 : Broken Access Control
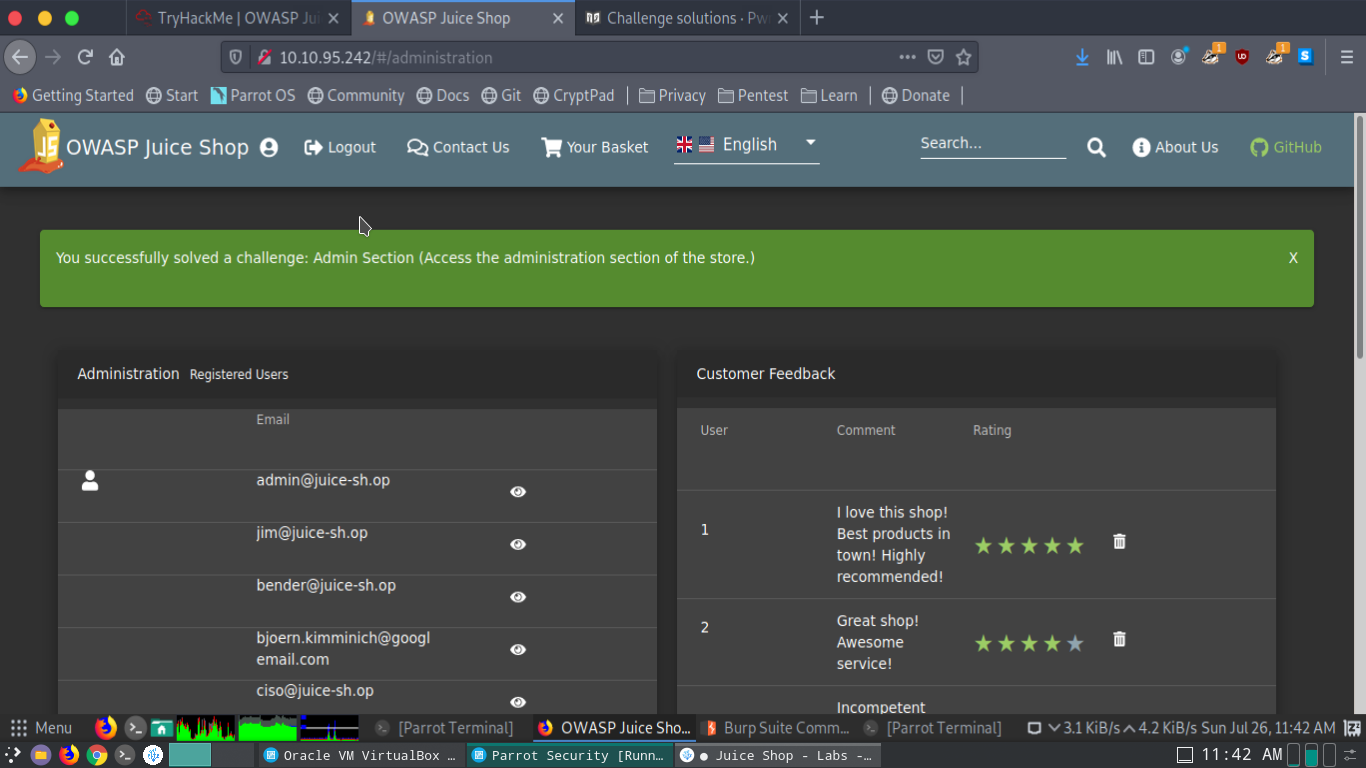
Access the administration section of the store - What is the name of the page?

main.js was loading in as a js file I used ctrl+f to find admin to find the administration page
Access someone else’s basket

In the storage section of inspect element and local session storage there is a bid element with a value.Change the bid value and refresh the page. This allows you to view another users basket.
Get rid of all 5 star customer feedback
In the administration page, the feedback is listed on the right with a trash icon next to it click on that to remove the appropriate feedback.
Task 8 : Cross Site Scripting (XSS)
Carry out reflected XSS using Tracking Orders
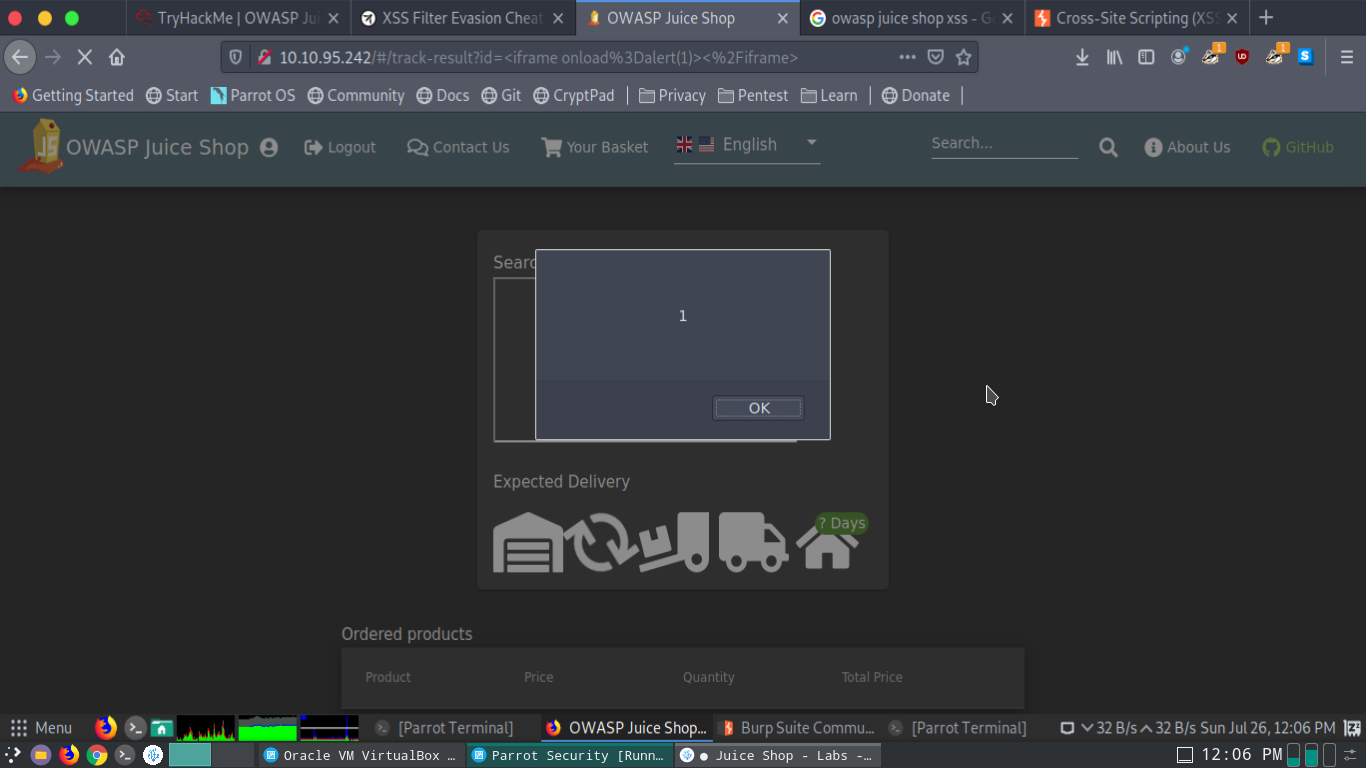
Opening the track your order page its a single field form and when you enter value it opens the next page.
<iframe onload="alert(1)"></iframe>
was the payload I used and worked well.
Carry out XSS using the Search field?
The search one wasn’t as easy so I used the technique I learnt on the portswigger labs.
I captured one of the search requests and sent it to intruder.

The search was in the url so I replaced the search term with
<>

The payload would be between the brackets. From the portswigger cheat sheet I copied the tags to use as payloads. Copy to clipboard and paste it in the payload section of intruder. Then I ran it.

Sorting the results by response size it was revealed that
<em>
gave a proper search result.
Then for the payload I simply looked through the cheat sheet and used
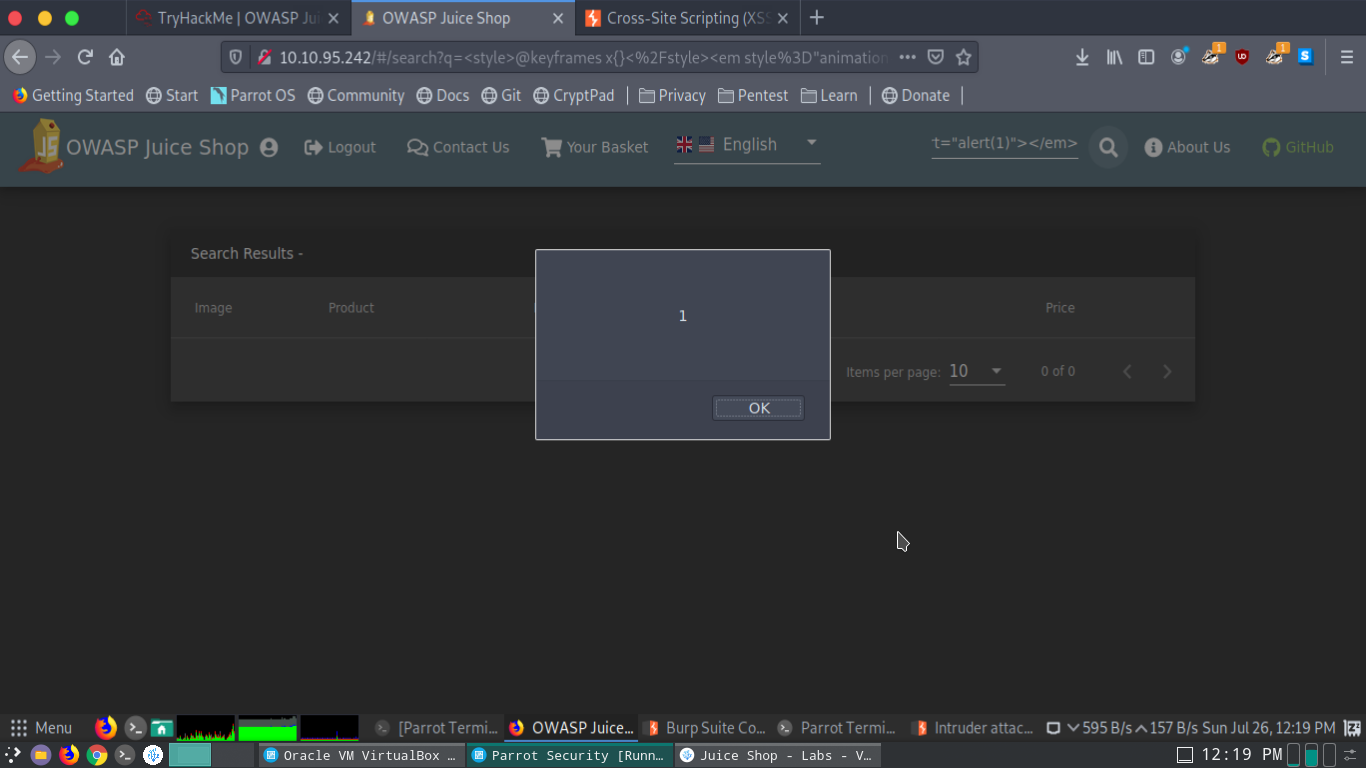
<style>@keyframes x{}</style><em style="animation-name:x" onanimationstart="alert(1)"></em>