This challenge was in the miscellaneous section of the challenges on Hackthebox. I was struggling with the scripting section during hacktivitycon and decided to do a writeup of this one.
I downloaded the challenge files and saw that it was a zip with a number as the name. Previewing the contents of the file revealed another zip file within it with what seemed like another random number. This seemed like a zip-ception kind of problem.
I manually tried to extract the first zip file but had to enter a password. Instantly I thought of brute forcing it using rockyou.txt.
I was going to use 7z to unzip the files incase there are other archive formats once I get the password. To brute the password I was going to use fcrackzip. (-u only displays the password)
fcrackzip -D -p /usr/share/wordlists/rockyou.txt 37366.zip -u
Much to my dismay got no valid password. Reading the docs/tutorials of fcrackzip I found another brute method that would brute numbers alone on the zip file as the password.
fcrackzip -b -v -c '1' -l 1-5 37366.zip -u
This would test numbers from 1 digit to 5 digits long. This gave me the password.
5900
Whats interesting here is that thats the name of the file within the zip we are trying to open.
7zip has a feature to display the files within an archive
7z l 37366.zip
Thereafter, I wrote a script to do extract the files.
#!/usr/bin/python3
from pwn import *
filename="37366.zip"
io = process('sh')
while 1:
print("filename="+filename)
if(filename == "6969.zip"):
break
io.sendline("7z l "+filename)
result = io.recvrepeat(1).decode().strip().split("\n")
#print("\n \n \n")
#print(result)
password=(result[-3].split(" ")[-1]).split(".")[0]
#break
print("password="+password)
io.sendline("7z e " + filename+ " -p"+password)
io.recvrepeat(1)
#io.recvline()
io.sendline("rm "+filename)
io.sendline("ls | grep zip")
ls =io.recvrepeat(1).decode().strip()
if ls == "":
break
filename=ls
print("newfile="+filename)
Initially I got through the zip-ception but that last file was a non-zip file that did not follow the password being filename. So it resulted in a empty file being created called DoNotTouch so I had to go through the process again keeping the additional code.
if(filename == "6969.zip"):
break
What I should have done is in the 7z l section I should have put a checker to not delete the file after extracting if it wasn’t a zip file.
So now I have a file DoNotTouch but the password is not the file name. Guess its time for rockyou.txt again.
This time it worked.

I checked the file type using
file DoNotTouch

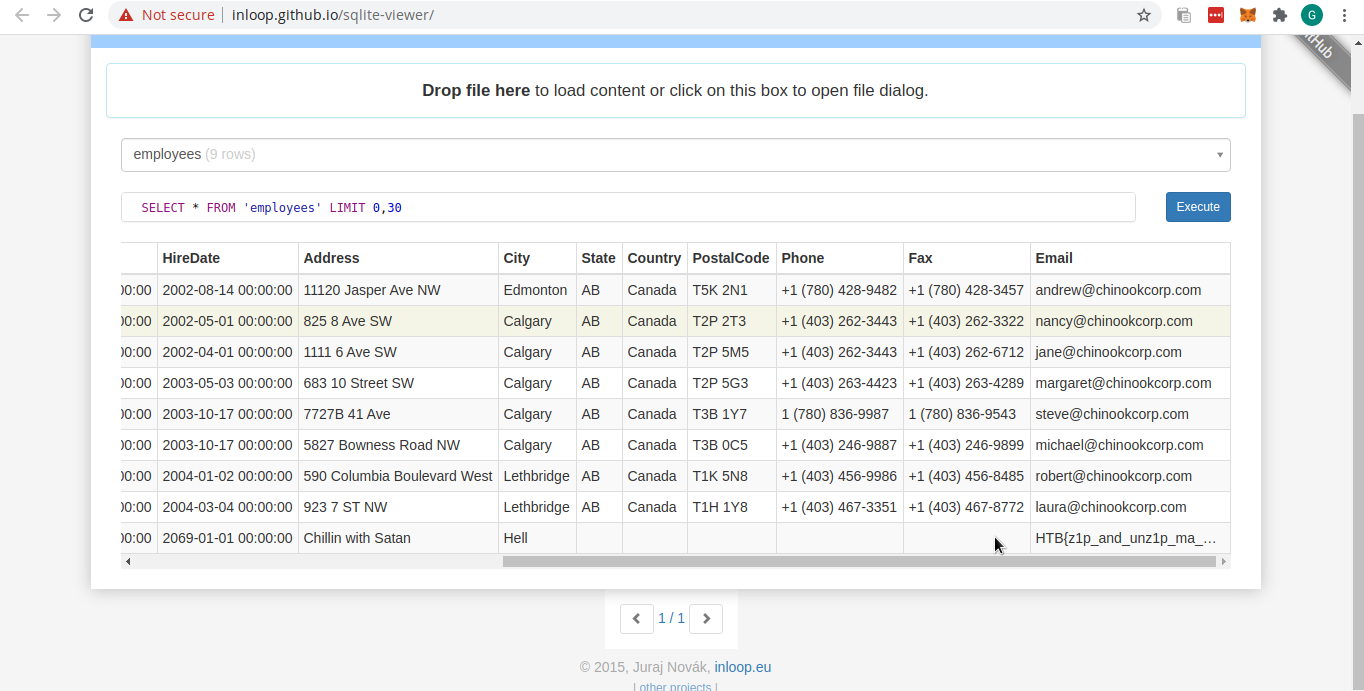
As always I prefer online tools so I looked online tools to able to view sqlite 3 data and found it here.
It was standard database format with tables and rows of table. There were quite a number of tables and while glancing through the table I found the answer.