People are the easier to hack than software.
According to the Verizon 2020 Data Breach Investigations Report
Credential theft and social attacks such as phishing and business email compromises cause the majority of breaches (over 67 percent), and specifically:
- 37 percent of credential theft breaches used stolen or weak credentials,
- 25 percent involved phishing
- Human error accounted for 22 percent as well.
For those that don’t know what I’m talking about I’m going to give you some background. You get an email from a Nigerian Prince who claims that he is desperate need for you help and if you give him your bank details and help him, he would send back a million dollars. Sound familiar? Thats essentially the most well known phishing scam.
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details, by disguising oneself as a trustworthy entity in an electronic communication. Since the inception of these scams technology has advanced a lot and so have the methods of these scammers. It’s not just emails and nigerian princes anymore. It’s evolved into social engineering which is essentially a psychological manipulation of people into performing actions or divulging confidential information by any means.
I’m going to break it down into the topics of general stuff, emails, websites, downloads, phones/messages, social media. What to be vary of and what not to do.
All of these topics bar the general one are in the format of a checklist that you can cross-reference on this page when you aren’t sure about the legitimacy of anything online.
NOTE: This is not an all exhaustive list that makes you invulnerable to scammers on the internet but covers a majority and keeps you vigilant of who and what you trust on the internet.
General
-
Updates. Keep everything updated, majority of updates are patches for security vulnerabilities so keep your browsers,anti-virus,operating systems and apps updated.
-
I use google.com as an anchor. When I type I focus more on speed than accuracy which often leads to a host of typos. So rather than typing in my bank website in the address bar I search it on google, which would probably be the first few links of the search. Google is not perfect but it is much more likely that the genuine website will appear and scammers websites with few typos and differences much further down in other pages of the google search if it hasn’t already been blocked by google or your browser.
-
Majority of attacks have financial motives. No bank or e-wallet will ask you to give them an password/otp/other data over the phone or via text message.
-
See what links you’re clicking on before you click on them. If you place your mouse over a link on a website/email or a button that goes to another website, you can see what the link is by checking the bottom left or right depending on which browser you use.

-
In the situation above it’s relatively simple, you hover over the link and know whether its genuine or not but the use of shortened links can confuse you as to whether they are genuine or not. From the google shortened links faq we can know "You can shorten URLs to make them easier to share using the Google URL shortener. For example, the short URL http://goo.gl/l6MS takes people to http://googleblog.blogspot.com/2009/12/making-urls-shorter-for-google-toolbar.html. "
What this means is that any link in the world can be compressed into a goo.gl google link. So stay away shortened links as they’re generally trying to hide something. Other services that shorten links include bitly, tinyurl.com and shorturl.at . They all follow the same principle of https://nameofservice/fewrandomcharacters and are easily identifiable mainly because they’re short in size. -
You should use different passwords for every website you register. Wherever possible activate 2-factor authentication so in addition to a password to sign in you would require an otp to your mail or phone or you can use an app like Google Authenticator. Follow the principle of long passwords with special characters,numbers and characters. Rather than using a string of random digits,numbers and characters what you can use are phrases instead so a password Dog$Cat$and2Hamster$ is easier to remember and well secured.
-
Given the number of registered websites and different passwords for each its not unrealistic that you won’t remember them. It’s not a security sin to have a password manager like lastpass or bitwarden or 1password. Make sure you have an extremely secure password and 2-factor authentication for these apps. If you want you can have a diary or notebook where you write but make it inconspicuous and keep it well protected and hidden. Please don’t write passwords on Post-it notes and stick it to the monitor.
-
If you are using a shared computer or laptop explicitly log out of all devices. Simply closing the tab or the browser will not log you out.
Websites
Websites should begin with “https://” and NOT “http://”. The default setting in most browsers is to only allow you to visit https websites. The ‘s’ at the end stands for secure. It essentially makes sure that that the data between you and the server/website is encrypted so that no one else can eavesdrop. It’s essentially making sure you a private conversation. However, be vary you could be having a private conversation with the devil.
Website links are complicated and are generally of the format (Sorry this is kinda technical) “https://subdomain.subdomain.domain.com/randomtextandnumbers”. If they are like “https://www.google.com” it’s not an issue. However, scammers will try to include a common name like Google and Microsoft in the format of “https://google.scam.com/” (Correct Gmail website is https://mail.google.com/). Note only the rightmost one is indicative of the website you’re currently on. It is the “domain” part of it as shown above. The website could end in .co.in or co. or .org or .edu or something else. These aren’t part of the name of website. I’m not going to bore you with the technical jargon behind it but “www.chase.com” is chase bank but “www.chase.bk” or “www.chase-bank.com” is not chase bank. They contribute to the uniqueness of a link.
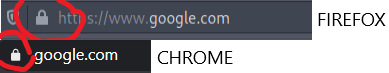
Look for a lock sign next to the website URL in the top part of the browser. This means it is https but again all it does is ensure that the communication is private not verify who exactly it is.
Reputed websites will have portals for credit/debit card payments or other methods. If bank transfer is the only option it is suspicious.
To replicate an official website takes a lot of hard work and effort. Everything needs to on point. Keep an eye out for if they’re asking you to input unrelated details or the site looks different to what you’re used to or typos.
Downloads
Stay away from piracy. It’s an easy target for scammers to people trying to download pirated movies or software. Majority of these websites that claim to have premium stuff for free are malware or viruses. Even device drivers should only be found on official websites and not third party websites.
A common scam is banners or websites telling you that your device has been infected by a virus and you should download a anti-virus from their website. No website can scan your system like that and identify viruses. Anti-viruses are downloaded and installed and cannot be done from your browser. You should simply close that tab or the browser.
If a file ends in a .exe it is an application file. .pdf, .xlsx, .docx and so on are documents. If a file claims to be a picture or pdf but ends in a .exe it should not be opened.
For downloaded files or any folder on your system you can right click on it and scan with windows defender or whichever anti-virus you are using. Make sure it’s updated and if it is malicious you will get to know that.
Emails
Unknown Sender: First line of defence. Any email-id you don’t recognize offering you something without you signing up for it? Delete and/or report sender. If it sounds too good to be true it probably is.
Check the email address of the sender: Lets say it’s Twitter telling you that you’ve signed in on a new device. All you see in your inbox is Twitter. The images below show you how to check the email address of the sender in gmail and outlook. More often than not scammers will use emails like ‘Twittter’ with an odd letter or number different. Attention to detail here helps. If you’re unsure about this please google the email which will probably give you more information.
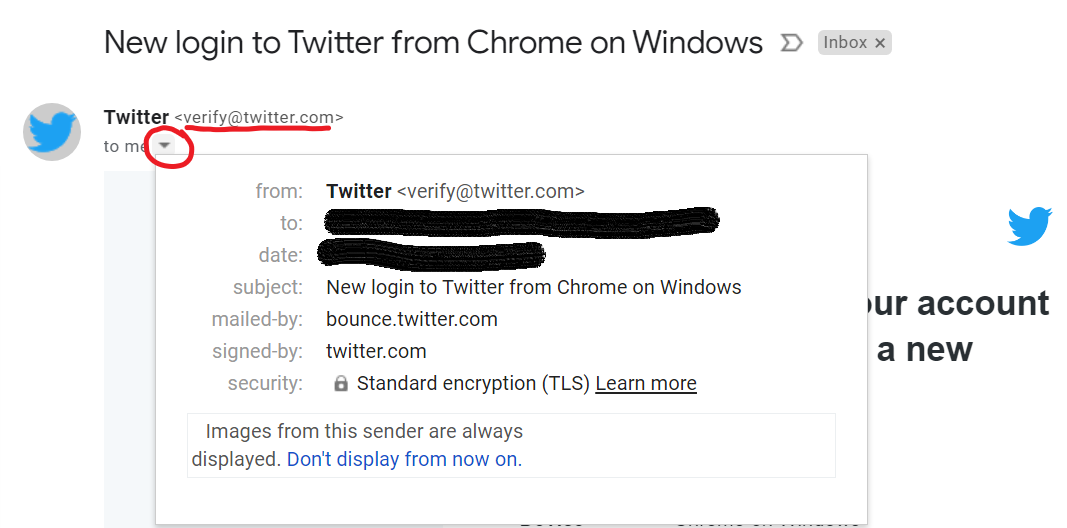
For gmail users once you open the mail you can see the address and click on the circled button to see more info.
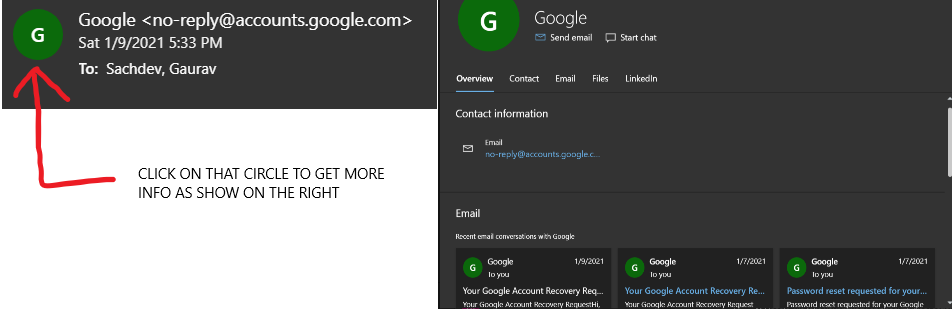
For outlook users once you click on the mail which opens on the right hand side it shows the entire id. You can click on the circle to see past conversations if you have had any which is useful.
From General we know how to check links by hovering over them and what shortened urls are. Any email that contains password reset links or website links via a shortened url is extremely suspicious. More often than not they are trying to hide fake/scam websites. But if its a standard website to go to the homepage of say chase bank its better to go via google or type it than let the email link take you there.
Unusual Grammar or Timing: Notice common spelling errors or weird/wrong grammar or word selection. Is it unusual timing like billing invoices in the middle of the month when you usually get it at the start of the month?
Phones
This one is a little more tricky as scammers have restored to targeting phones simply because they get a better success rate.
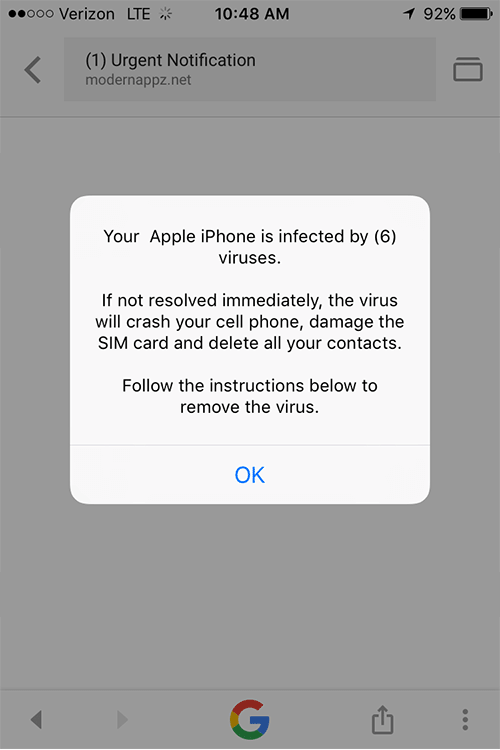
- ADVERTISEMENTS. Most of these are flashing signs saying you have a virus. When you click on them, they’ll tell you to download an “anti-virus”. This is actually malware that they then use to infect your data. An example of this is shown below. These malicious ads are on webistes as well as on phone apps.
-
PERMISSIONS. Okay so this is a new one that both Apple and Google have implemented. The apps have to explicitly ask for your permission to use your camera, your contact lists and so on. When you see a calculator app that wants access to your microphone and/or your contact lists, alarm bells should be going off in your head. This is more of a intuitive thing, you need to question whether an app needs that permission to function and if they refuse to boot up without those unnecessary permissions I would stay clear of it.
-
DOWNLOADS. Same principle as for computers, stay away from piracy and downloading apps that are not from the apple store or the google play store. Don’t download unnecessary files even documents like pdfs and docx files can have malware hidden in them.
-
RESPONSIVE TEXTS/CALLS. If you get a call/sms from the police department/tax office saying you’re wanted for questioning/tax evasion and a number/email is attached to the message and you’re supposed to call back or reach out on the number they wrote, it may be a scam. If you are genuinely concerend then google the phone number of the police department/tax department and give them a call to verify the claim made to you. Be careful of Amazon employees claiming they are giving you a free iphone for being a valued customer. If it sounds too good to be true it probably is.
Social Media
This is a particularly growing target for scammers.
-
A lot of the same vigilance applies here, be careful of people offering good deals on merchandise, extremely forward sexual advances, people you don’t know going out of their way to make friends. A common indicator is if that account follows a lot of people, but a lot of people don’t follow them and no profile pictures. People often impersonate celebrities or people you know so keep an eye out for that.
-
In general, the line between fake accounts and real accounts is often very blurred. It is better to be extra cautious, and you should default to assuming it is a fake account if there is a doubt.
Feel free to drop a comment and I can answer more questions if you have more questions as to the authenticity of things!